- Find Answers
- :
- Using Splunk
- :
- Other Using Splunk
- :
- Alerting
- :
- how to exclude several user activity from alert
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi All,
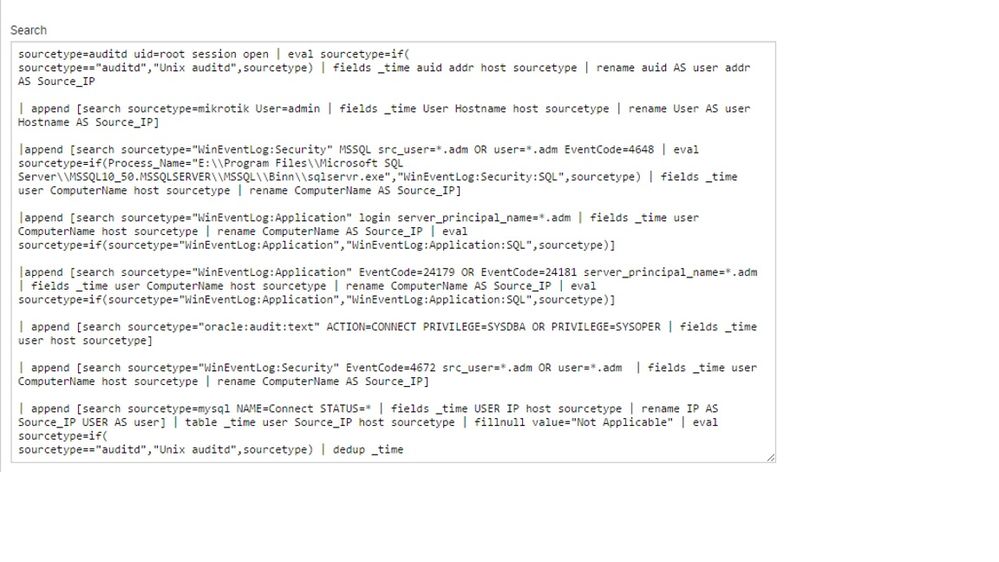
we use splunk to monitoring super user activity (on windows, DB, and network)
right now we have setting splunk to sending alert on several windows event code with .adm user. but now we want to exclude several user activities, so if the user doing activities on windows, splunk will not send the alert.
example we have user1.adm, user2.adm, user3.adm and right now if all user login on server, then splunk will send alert, but we want to exclude user3.adm. so if the user3.adm login, splunk will not send alert.
can someone help me, what query i need to add on my search alert on splunk?
note i need to exclude several user on all my DB, OS, Network, and the user is different in all the os, network and DB
please advice
Thanks,
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If there are many users in the exclusion list, your best option would be to create a lookup file/kvstore (http://docs.splunk.com/Documentation/Splunk/6.5.0/SearchReference/Lookup) and use that to exclude from your final list. Since you are using sub searches (append), it may be more effecient to just exclude from the final list. For example, lets assume your lookup file is called excludelist.csv, with a field named "user" then you could add something like this to the end of your query exclude users
.... | search NOT [| inputlookup excludelist.csv | field user ]
You could also do the filtering in each of your sub-searches, I just think that could be less efficient, depending on number events filtered by the users.
Having said this, I would strongly recommend against using sub-searches. Its just very slow and has limitations that could cause incorrect results. Look at this post here by @MuS on how you can achieve similar results without the use of sub-searches.
https://answers.splunk.com/answers/129424/how-to-compare-fields-over-multiple-sourcetypes-without-jo...
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If there are many users in the exclusion list, your best option would be to create a lookup file/kvstore (http://docs.splunk.com/Documentation/Splunk/6.5.0/SearchReference/Lookup) and use that to exclude from your final list. Since you are using sub searches (append), it may be more effecient to just exclude from the final list. For example, lets assume your lookup file is called excludelist.csv, with a field named "user" then you could add something like this to the end of your query exclude users
.... | search NOT [| inputlookup excludelist.csv | field user ]
You could also do the filtering in each of your sub-searches, I just think that could be less efficient, depending on number events filtered by the users.
Having said this, I would strongly recommend against using sub-searches. Its just very slow and has limitations that could cause incorrect results. Look at this post here by @MuS on how you can achieve similar results without the use of sub-searches.
https://answers.splunk.com/answers/129424/how-to-compare-fields-over-multiple-sourcetypes-without-jo...
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@sundareshr thanks for the help.
also thanks for the tips on the using sub-searches