Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Alerting
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Find Answers
- :
- Using Splunk
- :
- Other Using Splunk
- :
- Alerting
- :
- how can I do to create one search when I can see t...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
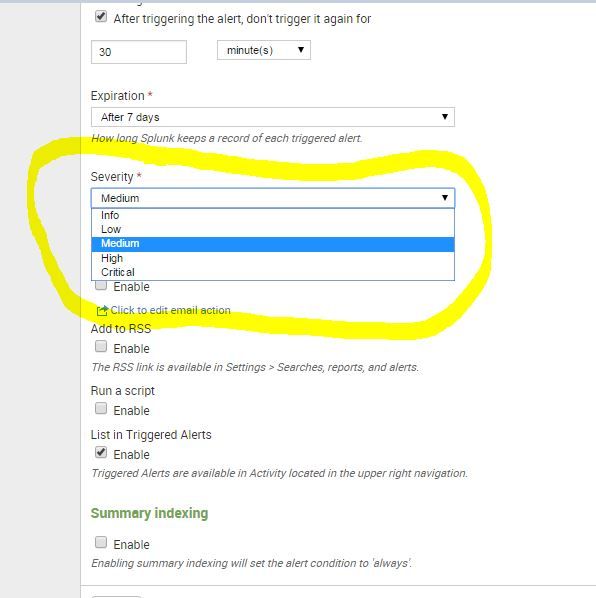
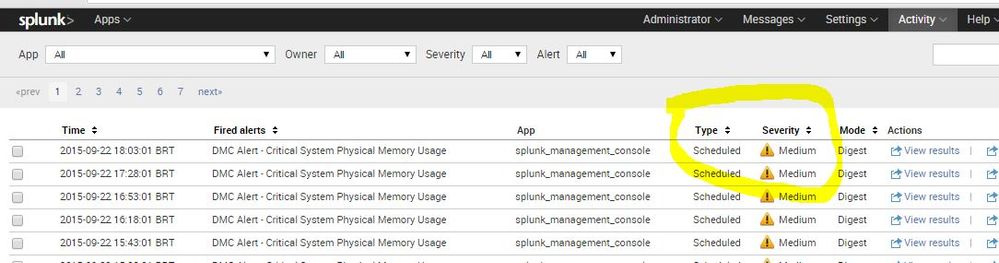
how can I do to create one search when I can see the severity of the alert?
samir_silva
New Member
09-22-2015
02:31 PM
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
gcato
Contributor
09-22-2015
05:19 PM
Hi Samir,
You can use the REST API to get this result. For example:
| rest /services/alerts/fired_alerts/-
|stats sum(triggered_alerts) AS count BY savedsearch_name, severity
|eval severity = case(severity==1, "Info",
severity==2, "Low",
severity==3, "Medium",
severity==4, "High",
severity==5, "Critical")
|rename savedsearch_name AS Alert
|table Alert severity count
Hope this helps.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
samir_silva
New Member
09-24-2015
06:28 AM
Tranks for help,
My finish search.
| rest https://localhost:8089/servicesNS/your-user/-/alerts/fired_alerts/- |stats sum(triggered_alerts) AS count BY savedsearch_name, severity
|eval severity = case(severity==1, "Info",
severity==2, "Low",
severity==3, "Medium",
severity==4, "High",
severity==5, "Critical")
|rename savedsearch_name AS Alert
|table Alert severity count
|sort - count
Get Updates on the Splunk Community!
Infographic provides the TL;DR for the 2024 Splunk Career Impact Report
We’ve been buzzing with excitement about the recent validation of Splunk Education! The 2024 Splunk Career ...
Enterprise Security Content Update (ESCU) | New Releases
In December, the Splunk Threat Research Team had 1 release of new security content via the Enterprise Security ...
Why am I not seeing the finding in Splunk Enterprise Security Analyst Queue?
(This is the first of a series of 2 blogs).
Splunk Enterprise Security is a fantastic tool that offers robust ...