- Find Answers
- :
- Using Splunk
- :
- Other Using Splunk
- :
- Alerting
- :
- How to create an Alert based off basis of threshol...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to create an Alert based off basis of threshold?
Hello Splunkers,
As per the below details i need to create an alert on the basis of threshold value. But in this case every offeringID has different rate. So how can i calculate the threshold for each offeringID and how can I map this under an alert as a generic thershold value. Please suggest some ideas on this.
As well as if any one aware about in dat -incache-memory in Splunk.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Store the threshold for each Offering_id in a csv store and do a lookup against the Offering_id in the event and compare the event rate with the stored rate.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@ITWhisperer But how can define the threshold for each offeringID here?. Every offeringID must have different threshold.
Threshold value should be dynamic for each value. So I am unable to understand how can i apply this.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What do you mean by rate? How do you calculate this? Where does the threshold come from?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
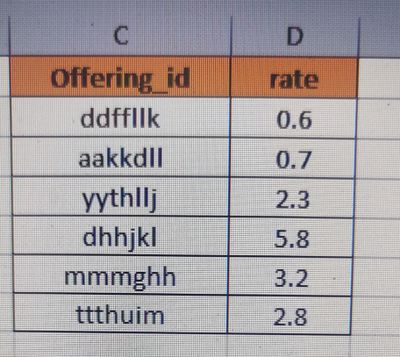
@ITWhisperer I have attached one screenshot. Please check this at once for the rate calculation.
We are taking the sum of all the highrisk event and then divided it by total number of events.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So, your threshold is just your rate rounded to 2 decimal places?
Do you recalculate highRisk in the stats along with total by Offering_id?
What do you want to alert on?
A clearer definition of what you are trying to achieve would help.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So, your threshold is just your rate rounded to 2 decimal places? ----Yes that is the threshold
Do you recalculate highRisk in the stats along with total by Offering_id? ----Yes, I have calculated from offereingID
What do you want to alert on? ---I want an alert triggred for top 10 offering id on the basis of threshold.
A clearer definition of what you are trying to achieve would help.
I am confused on over what will be generic threshold i would be set.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
OK I am unclear about what you are alerting - alerts are usually when something out of the ordinary is detected. Your search seems to be just looking for the top 10 thresholds (as you have calculated them).
How often does this search run?
Do you want an "alert" every time it runs?
If not, under what circumstances do you want an alert raised?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
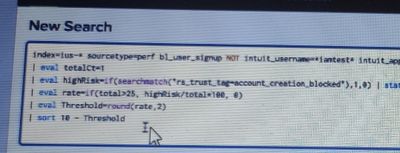
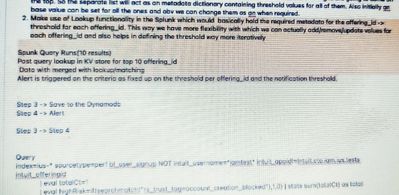
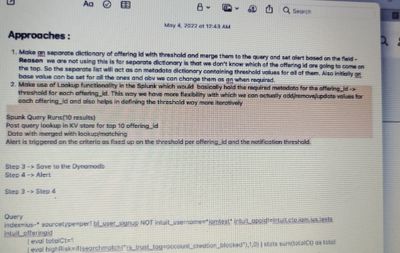
I have attached the screenshot of my requirement. I hope the screenshot is clear to you.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
OK so you need to set up a csv store with the various thresholds for each Offering_id
You can then use the lookup command in your search to retrieve the corresponding threshold for each Offering_id returned by your stats.
You could then compare your calculated rate against the stored threshold and calculate the variance. Is difference sufficient or do you need to take standard deviations from a mean for example?
You might then sort the variance in descending order to get the top 10 rates higher than their threshold.
Having said that, I am not sure how close this approach is to your requirement because your requirement seems unclear to me (and I suspect to you too!).
Why only store the top 10 in the kv store? What happens when a different Offering_id enters the top 10 (and there is no threshold stored for it)? The criteria for the alert is not clear enough - how often does your alert have to run? how many Offering_ids need to breach their threshold for the alert to be triggered?