- Splunk Answers
- :
- Using Splunk
- :
- Alerting
- :
- How can i add alert to my search query using trigg...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How can i add alert to my search query using trigger condition alert
Hi, Im setting up an alert for data flow the alert build is when the application is not running it will send us an alert and i use trigger condition in the alert.
here is the search query
| eval value1=if(like(sample, "value1"), 1,0), value2=if(like(sample, "value2"), 1,0), value3=if(like(sample, "value3"), 1,0)
| stats sum(value1) as VALUE1, sum(value2) as VALUE2, sum(value3) as VALUE3
| table VALUE1, VALUE2, VALUE3
and for the alert condition i use this command
search VALUE1 = 0
"0" because in the sum it indicates that the 0 means data is not flowing in splunk meaning the application is down
Thanks in advance
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi thanks for the answer, but im still not able to receive alerts 😞 im using email alerts
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How have you set up your alerts?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
here is my original query
| eval amd-eu1=if(like(namespace, "amd-eu1"), 1,0),
amd-eu2=if(like(namespace, "amd-eu2"), 1,0), amd-eu3=if(like(namespace, "amd-eu3"), 1,0), amd-eu4=if(like(namespace, "amd-eu4"), 1,0),
amd-eu5=if(like(namespace, "amd-eu5"), 1,0), amd-ap1=if(like(namespace, "amd-ap1"), 1,0), amd-am1=if(like(namespace, "amd-am1"), 1,0)
| stats sum(amd-eu1) as AMD_EU1, sum(amd-eu2) as AMD_EU2, sum(amd-eu3) as AMD_EU3, sum(amd-eu4) as AMD_EU4, sum(amd-eu5) as AMD_EU5, sum(amd-ap1) as AMD_AP1, sum(amd-am1) as AMD_AM1
i have remove the table
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
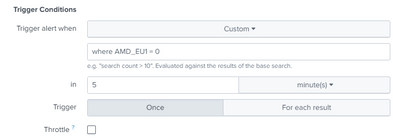
I use this and it is realtime
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Rather than custom, can you use number of results returned by the search?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
But due to the stats sum and the value inside it a table will be created then it will be a result for the search
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Put the where as part of your search rather than the custom condition on the alert
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, Sorry for the late reply the alert works but it was spamming a lot of mail and also even though the data is flowing it is still alerting
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You might want to use
| where VALUE1=0then you can alert on whether there are any results or not