Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- how to modify my query to display a detail view wi...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
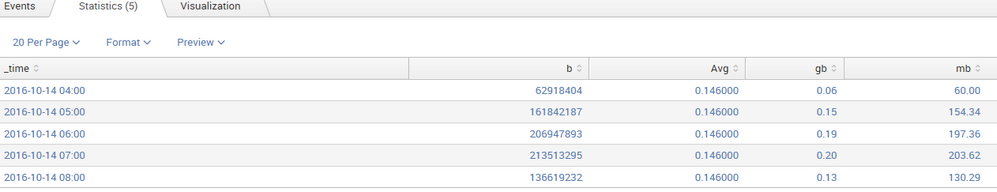
I have a search as follows
field="abc"| eval b=len(_raw) | timechart span=1h sum(b) as b | eval mb=round(b/1024/1024,2) | eval gb=round(b/1024/1024/1024,2) | eventstats avg(gb) as Avg
Which displays the result as follows
Now I want to modify my search to see a time chart which displays the average gb for each host per hour. Is there any way to modify my search to display like that?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The trick is that you need to do the "bucketing" that timechart does, twice: once to calculate each hosts's hourly sum and then again to avg all hosts' sums. This is a exactly why the bucket (AKA bin) command exists. Do it like this:
field="abc"| eval b=len(_raw)
| bucket _time span=1h | stats sum(b) AS b by _time host
| timechart span=1h avg(b) as b | eval mb=round(b/1024/1024,2) | eval gb=round(b/1024/1024/1024,2)
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The trick is that you need to do the "bucketing" that timechart does, twice: once to calculate each hosts's hourly sum and then again to avg all hosts' sums. This is a exactly why the bucket (AKA bin) command exists. Do it like this:
field="abc"| eval b=len(_raw)
| bucket _time span=1h | stats sum(b) AS b by _time host
| timechart span=1h avg(b) as b | eval mb=round(b/1024/1024,2) | eval gb=round(b/1024/1024/1024,2)
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Based on your indications above:
I want to modify my search to see a time chart which displays the average gb for each host per hour
I guess this is what you are looking for:
field="abc"
| eval b=len(_raw)
| timechart span=1h avg(b) as b by host
| foreach * [eval <<FIELD>>=round('<<FIELD>>'/1024/1024/1024,10)]
NOTE: I have rounded that to include up to 10 decimals mainly because I don't know how much data is going through your hosts but feel free to revert that back to 2 o whichever value fits your needs.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
field="abc"| eval b=len(_raw) | timechart span=1h sum(b) as b | eval mb=round(b/1024/1024,2) | eval gb=round(b/1024/1024/1024,2) | eventstats avg(gb) as Avg by host
Sekar
PS - If this or any post helped you in any way, pls consider upvoting, thanks for reading !
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi sorry there isn't any change in my result.