- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- WILDCARD in LookUp .csv files
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi all,
I have a challenge, that i have been struggling for the past few days, and can't find the correct solution.
I have read
and done pretty much exactly the same thing, but it doesn't work for me. So here are the details.
I have a simple lookup csv file (2 columns ), first one with starting digits
prefix, state
23401*, log1
23402*,log2
34602*,log5
....etc
I have used the GUI to create the lookup definitions, but i have also double-cheked transformes.conf and props.conf. It is exactly as in the example in the link. I can't make the wildcard work for me.
Here is a simple search line just to illustrate
source="log2.log" host="prod-splunk-indexer" sourcetype="testsource" |
lookup prefixlookup.csv prefix OUTPUT state |
table prefix state
If i create lookup with exact matches, it works for the match everytime, however, my client requires only prefixchecks, and to me WILDCARD is the only solution.
Any ideas?
PS.
I have actually created exact replica of the case(user,username, userlookup, etc) in the linked example, still doesn't work
Have a great day!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi all,
I have to say , I found the issue that was bugging me. As suggested, it was something simple , that was in front of me all the time.
Here is what didn't work:
sourcetype="log2" | lookup ranges.csv comment OUTPUT state | table comment state
And here is what worked:
sourcetype="log2" | lookup ranges comment OUTPUT state | table comment state
I can't believe I didn't figure it out earlier, but hey, learning is a process 🙂
Thanks!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @boromir
Can you try the below,
Go to Lookup definition --> Advanced options --> Match Type, and enter WILDCARD(FieldName)
FieldName - The field which consists of wild card in the lookup file.
Check and let me know if you still come across any issues.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Thanks for responding:)
Exacltly the same. I feel like I am missing something. I can't even make the example work.
As mentioned, I am now fighting to make the example from the link to work, and have completely put my put my case on the backburner. So here is what i have , and doesn't work:
userlookup.csv
user,username
user*,USERNAME
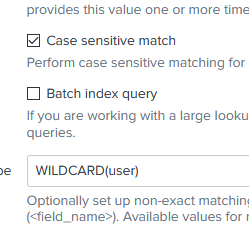
transforms.conf
[userlookup]
batch_index_query = 0
case_sensitive_match = 1
filename = userlookup.csv
match_type = WILDCARD(user)
Props.conf
[log2]
LOOKUP-user = userlookup user OUTPUT username
...And for the full picture :
I think that the solution is in front of my eyes, but I fail to see it.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you elaborate your requirement a bit more,
So you want to filter your results with the prefix field values in the csv and again assign a state field value to the results?
If above is your requirement, try the below query.
source="log2.log" host="prod-splunk-indexer" sourcetype="testsource" prefix=*
[| inputlookup prefixlookup.csv
| table prefix]
| lookup prefixlookup.csv prefix OUTPUT state
| table prefix state
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Thanks, I will try to explain it better.
My client provides me a table(csv 1000x lines , 2 columns) with prefixes that I will be able to find in the logs from the monitored equipment. Based on those prefixes, I have to structure them, assign them new values, which we will use later. Based on what I have read, Lookup with wildcard in the lookup table is the solution to my challenge, and based on https://community.splunk.com/t5/Splunk-Search/Can-we-use-wildcard-characters-in-a-lookup-table/td-p/...
I should be able to get exactly what i need, however , it still doesn't work.
I have tested your example, but it gets me exactly the same result. The wildcard does not match.
Kind regards!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi all,
I have to say , I found the issue that was bugging me. As suggested, it was something simple , that was in front of me all the time.
Here is what didn't work:
sourcetype="log2" | lookup ranges.csv comment OUTPUT state | table comment state
And here is what worked:
sourcetype="log2" | lookup ranges comment OUTPUT state | table comment state
I can't believe I didn't figure it out earlier, but hey, learning is a process 🙂
Thanks!