Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Splunk search command- How to get table?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
Assuming i have numbers, let's say 1-2-3-4-5-6. And each of those represent
| Ip adress | number of request | method |
| 1.1.1.2 | 1 | get |
| 1.1.1.3 | 1 | get |
| 1.1.1.4 | 2 | get |
| 1.1.1.5 | 4 | get |
| 1.1.1.6 | 4 | get |
| 1.1.1.7 | 5 | get |
| 1.1.1.8 | 7 | get |
What's could be the search to get following table
| number of requests | number of IPs that make 'x' requests |
| 1 | 2 (meaning to client has made 1 requests) |
| 2 | 1 |
| 3 | 0 |
| 4 | 2 |
| 5 | 1 |
| 6 | 0 |
| 7 | 1 |
| 8 | 0 |
| 9 | 0 |
Thanks
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
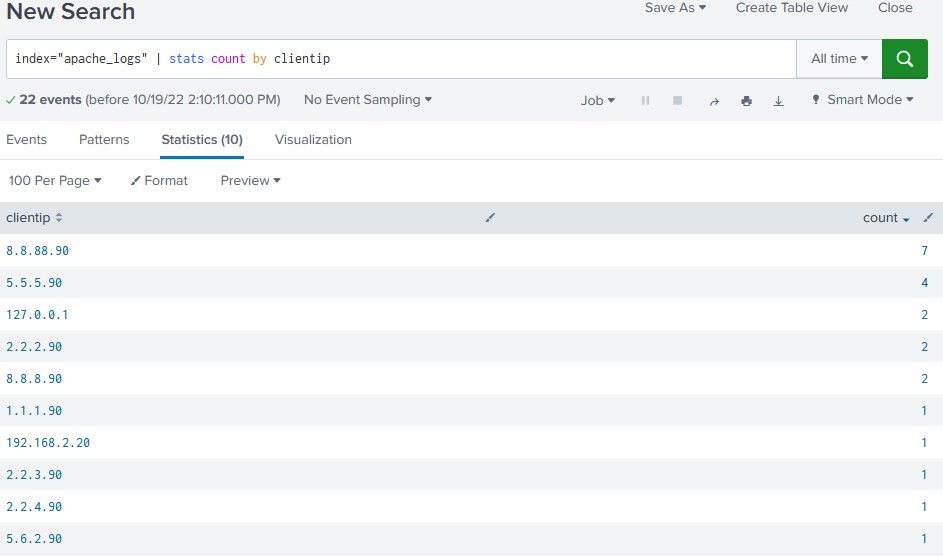
Hy
I took a picture to illustrate a bit what I would like to do.
Basically I want to do this :
how many client have made 1 requests ?
how many client have made 2 requests ?
how many client have made 3 requests ?
... so on and so forth ...
Take the data in the `count` column and the `clientip` column and sort them with a search so as to answer my questions above.
The final table should look something like this:
| nb_requests | Total_client |
| 1 | 7 |
| 2 | 2 |
| 4 | 1 |
| 7 | 1 |
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just add something like:
| stats count as clientcount by count
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello boss,
Your tips helped out.
very glad now 🙂
Thank you for the help.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @dj56,
good for you, see next time!
Ciao and happy splunking
Giuseppe
P.S.: Karma Points are appreciated by all the Contributors 😉
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oh sorry
Yes i tried but i didn't get what i want. Probably because i don't have i field called "number_of_requests" as that digit result from a search count.
Thank you for your help.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @dj56,
tell me if it's all clear for you and please accept one answer for the other people of Communty.
otherwise, please share your search to help you more.
Ciao.
Giuseppe
P.S.: Karma Points are appreciated 😉
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @dj56,
you can use stats dc to find the number of distinct occerrences for each number of requests.
The main problem is when there isn't any occurrences, so you have to define the max number of occurrences to display.
So you have to define the maxnumber of occurrences, fine in this sample:
index=_internal | head 100
| stats dc(source) AS dc BY linecount
| append [ | makeresults count=5 | streamstats count AS linecount | eval dc=0 | fields - _time ]
| stats sum(dc) AS total BY linecountin your case, if the max number of requests is 10, you could have:
<your_search>
| stats dc(ip) AS ip_count BY number_of_requests
| append [ | makeresults count=5 | streamstats count AS number_of_requests | eval ip_count=0 | fields - _time ]
| stats sum(ip_count) AS total BY number_of_requests Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You need to run stats to count the number of distinct ip address against the "number of requests". Let's assume your fieldnames are "ip address" and "method":
<base_search>
| stats count as "number of request" by "ip address" method
| stats dc("ip address") AS "number of IPs that make requests" BY "number of request" method