Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: How to separate data from Security_ID field wh...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
I am trying to test on a single host and this search may be completely wrong and would appreciate any assistance as I am just starting to use Splunk.
I am trying to capture any local accounts created or added to the local Administrators group on one host.
This gets me what I need, which is the Time(when), hostname ,who created but the Security_ID field is lumping all into one .. I need a column with just the Hostname\LocalAccountName or just LocalAccountName
Security_ID is including the SAmAccountname that created the account, the local account name and BUILTIN\Administrators all in one.
This is what I am searching, any help will be appreciated.
MyHostName EventCode=4732 OR EventCode=4720 | table _time, HostName, src_user, Security_ID, EventCode,- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
MyHostName EventCode=4732 OR EventCode=4720
| eval group_sid=mvindex('SecurityID',2)
| table _time, HostName, src_user, group_sid, EventCode
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Marcy
The example log you posted is the exact that I see , I tested your example below but it made no difference .. is that how I would search ?
MyHostName EventCode=4732 OR EventCode=4720 | table _time, HostName, src_user, Security_ID, EventCode
|eval group_sid=mvindex('SecurityID',2)
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
MyHostName EventCode=4732 OR EventCode=4720
| eval group_sid=mvindex('SecurityID',2)
| table _time, HostName, src_user, group_sid, EventCode
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
that was it , I modified it a bit and got the
I modified ('SecurityID',2) to ('Security_ID',1)
MyHostName EventCode=4732 OR EventCode=4720
| eval group_sid=mvindex('Security_ID',1)
| table _time, HostName, src_user,group_sid
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
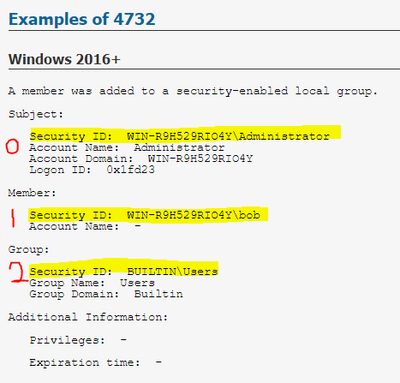
Your problem I think, is that SecurityID is a multivalue field.
For reference: https://www.ultimatewindowssecurity.com/securitylog/encyclopedia/event.aspx?eventid=4732
If you want to extract these into individual fields you would use "mvindex":
|eval subject_sid=mvindex('SecurityID',0)
|eval member_sid=mvindex('SecurityID',1)
|eval group_sid=mvindex('SecurityID',2)
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content