Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: How to get the status wise data
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
I wrote below query which gives me data per service per min...
index=**** | bucket _time span=1m | convert ctime(_time) AS Hour timeformat="%H:%M" | stats count AS Requests by service, Hour
Below is the screenshot for same
the requests i wanted to split based on HTTP status code (200, 404, 302, 500 etc). I am using below query for same but i am unabe to get the data.
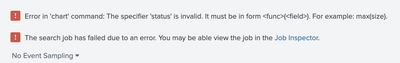
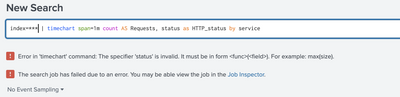
index=*** | bucket _time span=1m | convert ctime(_time) AS Hour timeformat="%H:%M" | chart count AS Requests,status as HTTP_status by service, Hour
error screen shot -
Can someone please help me how to get the number of requests by status code?
Thanks,
SG
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Not with chart - you can use stats however
| stats count by Hour service HTTP_status- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
chart (or timechart as @PickleRick suggested) doesn't work with 4 dimensions (time, service, status and count). if you want just status then use
| chart count AS Requests by HTTP_status, Hour
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@ITWhisperer Ahhh. You're right. I keep forgetting that and facepalm myself every so often 😄
Indeed, that's one of the cases where binning with time actually makes sense.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In this case i will not be able to bifurcate my stats service wise.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Not with chart - you can use stats however
| stats count by Hour service HTTP_status- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
First things first - you don't usually want to do bucketting and then stats by time because you have a specialized command for this - timechart
So your search may be rewritten simply as
index=***
| timechart span=1m count AS Requests status as HTTP_status by service
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ahhh, right. Forgot about that 🙂
Transforming commands need some form of aggregation function to be applied to fields. So you can't just give a simple field name. You can have count(status) or dc(status) or any other statistical function. In your case, I suppose values(status) will do.
Or if you want to further break down your results by status move the status from the aggregation to the "by" clause
| timechart span=1m count by status service
EDIT: As @ITWhisperer already mentioned, this solution is wrong because of two separate dimension used for classifying events for stats. So we can either use manual binning and statsing or we have another solution - we can create an artificial combined dimension:
| eval servicestatus=service."-".status
| timechart span=1m count by servicestatus