- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How to create an alert for when the VPN goes down ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi
I need to create an alert for when the VPN goes down but only when the drop lasts more than 1 minute.
I would appreciate your help
Right now I have the alert set to report any down events and then manually check which ones last longer than 1 minute.
index=paloalto |search EventID=tunnel-status-down OR EventID=tunnel-status-up
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
My first reply would not return results if the VPN was not down for more than a minute - I believe that's the expected scenario. Then the alert just has to be configured to trigger when the search returns results - meaning the the VPN has been down for at least one minute.
My answer also assumed events would be in reverse time order, which is the default for Splunk searches. Since your screenshot shows that's not the case, here is an updated search.
index=paloalto EventID=tunnel-status-down OR EventID=tunnel-status-up
| sort - _time
| dedup EventID Object
| where (EventID=tunnel-status-down AND _time < relative_time(now(),"-1m"))If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Look for where the last event is a status-down and it's been more than a minute since then.
index=paloalto |search EventID=tunnel-status-down OR EventID=tunnel-status-up
| dedup EventID
| where (EventID=tunnel-status-down AND _time < relative_time(now(),"-1m"))If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
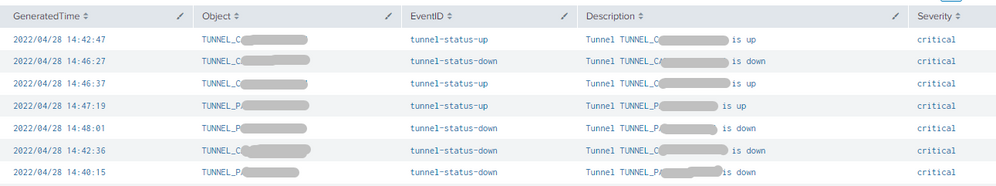
Hello, it did not bring me results.
This is the result when I only filter by the EventIDs, how can I calculate the time between the first down and the next up?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
My first reply would not return results if the VPN was not down for more than a minute - I believe that's the expected scenario. Then the alert just has to be configured to trigger when the search returns results - meaning the the VPN has been down for at least one minute.
My answer also assumed events would be in reverse time order, which is the default for Splunk searches. Since your screenshot shows that's not the case, here is an updated search.
index=paloalto EventID=tunnel-status-down OR EventID=tunnel-status-up
| sort - _time
| dedup EventID Object
| where (EventID=tunnel-status-down AND _time < relative_time(now(),"-1m"))If this reply helps you, Karma would be appreciated.