Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: Help with search to use for dashboard - link k...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Folks -
I would appreciate some help to create a dashboard. I want a simple line chart that shows how a value changes over time.
My data comes from a csv file and in the csv, is in this format:
| timestamp | mac_address | key | value |
| 20220902-153931 | xx:yy:zz:aa:bb:01 | counter_01 | 246897 |
| 20220902-153931 | xx:yy:zz:aa:bb:01 | counter_02 | 1595 |
Further on in the same file we see the same keys for a different device by mac_address:
| timestamp | mac_address | key | value |
| 20220902-153931 | xx:yy:zz:aa:bb:02 | counter_01 | 600 |
| 20220902-153931 | xx:yy:zz:aa:bb:02 | counter_02 | 1350 |
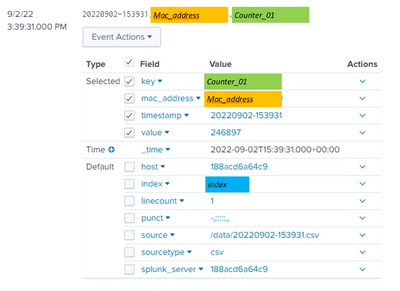
This is how the data looks in search for a single device (identified by mac_address) and a single key (counter_01) with a value of 246897.
These values are pulled via a script which runs according to a schedule, so the index will contain updated data with a new timestamp. In all there are about 20 key/value matches per device per run of the script.
What I would like to achieve:
A simple line chart that shows the values for device 1, showing the counter_01 key and how the value changes over time.
The problem I am having is understanding how to get the chart to identify the device and then show the right stat.
Once I know how to do this I'm sure I can work out how to display the other values.
As always, I'm very grateful for any help.
NM
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What you have there is looking for a match between the value in field 'key' and the value in field 'counter_01' - to compare the value in field 'key' with the string value "counter_01", you need to have the string value in double quotes (as I showed).
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am slightly confused by your example data and requirement - you have timestamps all the same (yet you want to show changes over time) - you have 3 mac addresses ending in 02 and 1 ending in 01 - the values for counter_01 are different, but the values for counter_02 are the same.
Charts would usually have 3 dimensions, _time / timestamp, value, series. Which of your fields represent these dimensions?
(You can use overlays to split some of the series into different scales, but the series are still the third dimension.)
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the reply.
I have made some corrections to the original post - thanks for bearing with me.
To keep it simple, if we look for now at just mac address 1, so for a single device (ie define the mac address to display for), I would like to track the time as the x-axis. The y-axis would be the value. The dataset would be counter_01.
I hope this clears things up - thanks again for the help.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
| where key="counter_01" AND mac_address="xx:yy:zz:aa:bb:01"
| timechart values(value) by key- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
OK, I have this:, but no results found:
| where index=index AND key=counter_01 AND mac_address="xx:yy:zz:aa:bb:01"
| timechart values(value) by key
(I added the index name)
Did I miss something?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What you have there is looking for a match between the value in field 'key' and the value in field 'counter_01' - to compare the value in field 'key' with the string value "counter_01", you need to have the string value in double quotes (as I showed).