Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Splunk Search
×
Are you a member of the Splunk Community?
Sign in or Register with your Splunk account to get your questions answered, access valuable resources and connect with experts!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: Duplicate Entries in Table
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
geekf
Path Finder
02-10-2021
04:15 AM
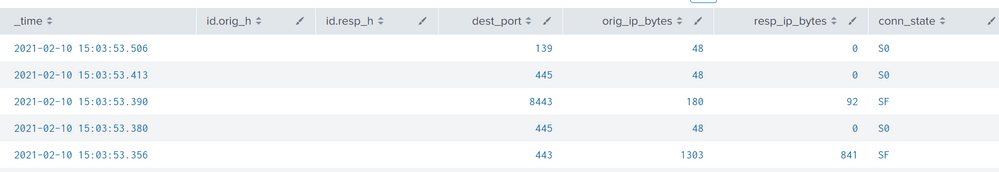
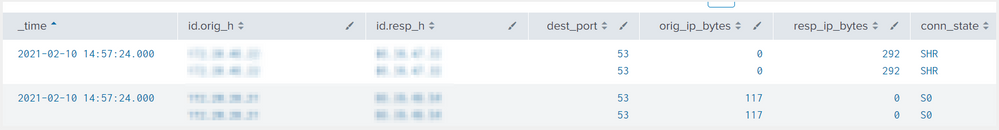
While using the table for bro conn data, I am getting duplicate data; however, if I use mvdedup, I get all the desired results except the id.orig_h and id.resp_h. If I use mvdedup for these two entries, I get blank values.
index=bro_conn
| eval id.orig_h=mvdedup(id.orig_h)
| eval id.resp_h=mvdedup(id.resp_h)
| eval dest_port=mvdedup(dest_port)
| eval resp_ip_bytes=mvdedup(resp_ip_bytes)
| eval orig_ip_bytes=mvdedup(orig_ip_bytes)
| eval conn_state=mvdedup(conn_state)
| eval proto=mvdedup(proto)
| table _time id.orig_h id.resp_h dest_port orig_ip_bytes resp_ip_bytes conn_state
Here are the results if I don't use mvdedup:
Is there a better way to dedup the results, and if this is the right way, how can I make this work for the src and dest IPs?
Thank you!
1 Solution
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
scelikok

SplunkTrust
02-10-2021
06:45 AM
Hi @geekf,
If complete event is duplicated, you can try dedup on _raw field;
index=bro_conn
| dedup _raw
| table _time id.orig_h id.resp_h dest_port orig_ip_bytes resp_ip_bytes conn_stateOtherwise try below;
index=bro_conn
| eval id.orig_h=mvdedup('id.orig_h')
| eval id.resp_h=mvdedup('id.resp_h')
| eval dest_port=mvdedup(dest_port)
| eval resp_ip_bytes=mvdedup(resp_ip_bytes)
| eval orig_ip_bytes=mvdedup(orig_ip_bytes)
| eval conn_state=mvdedup(conn_state)
| eval proto=mvdedup(proto)
| table _time id.orig_h id.resp_h dest_port orig_ip_bytes resp_ip_bytes conn_state
If this reply helps you an upvote and "Accept as Solution" is appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
scelikok

SplunkTrust
02-10-2021
06:45 AM
Hi @geekf,
If complete event is duplicated, you can try dedup on _raw field;
index=bro_conn
| dedup _raw
| table _time id.orig_h id.resp_h dest_port orig_ip_bytes resp_ip_bytes conn_stateOtherwise try below;
index=bro_conn
| eval id.orig_h=mvdedup('id.orig_h')
| eval id.resp_h=mvdedup('id.resp_h')
| eval dest_port=mvdedup(dest_port)
| eval resp_ip_bytes=mvdedup(resp_ip_bytes)
| eval orig_ip_bytes=mvdedup(orig_ip_bytes)
| eval conn_state=mvdedup(conn_state)
| eval proto=mvdedup(proto)
| table _time id.orig_h id.resp_h dest_port orig_ip_bytes resp_ip_bytes conn_state
If this reply helps you an upvote and "Accept as Solution" is appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
geekf
Path Finder
02-11-2021
03:52 AM
Thank you.
dedup _raw didn't work, single quotes for src and dest worked fine.
Get Updates on the Splunk Community!
Index This | What did the zero say to the eight?
June 2025 Edition
Hayyy Splunk Education Enthusiasts and the Eternally Curious!
We’re back with this month’s ...
Splunk Observability Cloud's AI Assistant in Action Series: Onboarding New Hires & ...
This is the fifth post in the Splunk Observability Cloud’s AI Assistant in Action series that digs into how to ...
Now Playing: Splunk Education Summer Learning Premieres
It’s premiere season, and Splunk Education is rolling out new releases you won’t want to miss. Whether you’re ...