Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Appending/Adding count of results in the column he...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
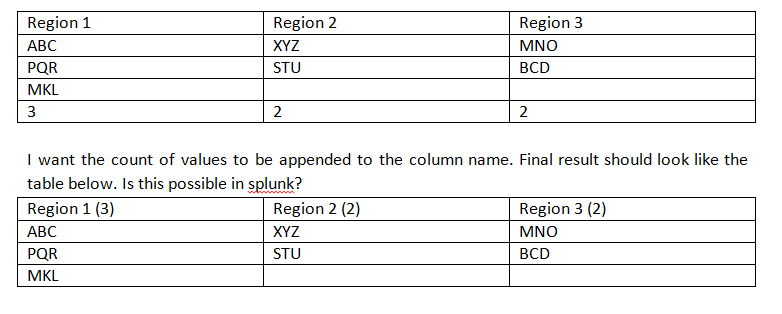
I have a search - index=ABC sourcetype=XYZ | stats values(user), dc(user) by region | transpose header_field=region | fields – column which produces the following result:
Region1 Region2 Region3
ABC XYZ MNO
PQR STU BCD
MKL
3 2 2
I want the count of distinct users to be appended to the column name in the table. Final result should look like the table below. Is this possible in Splunk?
Region1(3) Region2(2) Region3(2)
ABC XYZ MNO
PQR STU BCD
MKL
Added a picture of the table to make it clear
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Try this...
index=ABC sourcetype=XYZ
| stats values(user) as user, dc(user) as usercount by region
| eval region = region." (".usercount.")"
| fields - usercount
| transpose header_field=region
| fields – column
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@pushpender07, try the following:
index=ABC sourcetype=XYZ
| stats values(user) as user dc(user) as dc_user by region
| eval region=region."(".dc_user.")"
| transpose header_field=region
| search column=user
| fields – column
| makeresults | eval message= "Happy Splunking!!!"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
this one does not work, it just displays one row with user text in it. Response from @DalJeanis works perfectly
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have updated, it should have been values(user) and not last(user)
| makeresults | eval message= "Happy Splunking!!!"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
still does not work, what is the use of search column = user? It shows the same response with one row and "user" as text in it
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
| search column=user gets rid of column dc_user (count of distinct users) after transpose, since count is already appended to table header region. You can remove pipes 4, 5 and 6 and then put them back in the query one by one to understand what they are doing.
If results are not the way you expect, maybe I missed something you want. As far as there is another answer solving your problem you should be good!
| makeresults | eval message= "Happy Splunking!!!"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Try this...
index=ABC sourcetype=XYZ
| stats values(user) as user, dc(user) as usercount by region
| eval region = region." (".usercount.")"
| fields - usercount
| transpose header_field=region
| fields – column
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@DalJeanis...You beat me to it 🙂
| makeresults | eval message= "Happy Splunking!!!"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I was snoozing but we all 3 commented before @someshoni2!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@woodcock - you must have sneezed while typing @somesoni2.
... and it took all my self-control not to type "woodstock"...
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I answer to everything.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Perfect, thanks it works
