- Splunk Answers
- :
- Splunk Premium Solutions
- :
- Security Premium Solutions
- :
- Splunk Enterprise Security
- :
- Re: Splunk Enterprise Security: Drilldown stats li...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
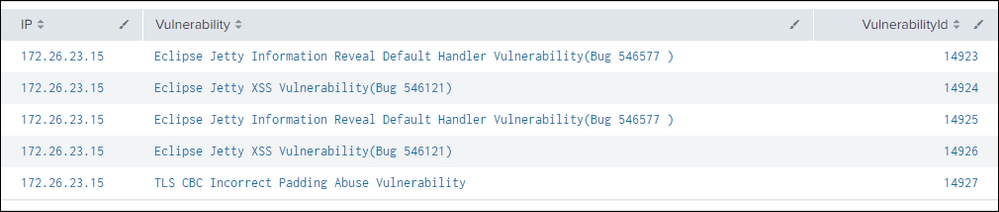
I am building a vulnerability dashboard and got the following table:
To make it easier to read I like to combine the IP addresses using
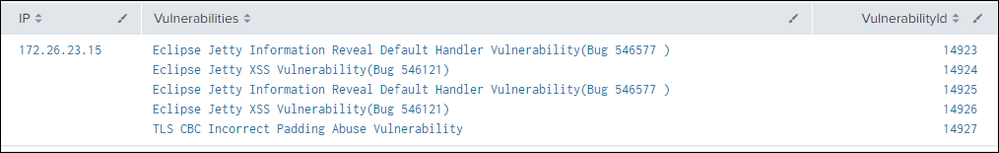
| stats list(Vulnerability) AS Vulnerabilities, list(VulnerabilityId) AS VulnerabilityId by IP
The VulnerabilityId is an internal unique Id that I like to hide from the user but I would like to add a drilldown that sets a token to this VulnerabilityId. In the first table I can achieve that by setting the a token to "$row.VulnerabilityId$". The problem is as soon as I use "stats list()" the token will include all VulnerabilityIds in the cell (14923,14924,14925,...).
- Is there a possibility to only set the one VulnerabilityId associated with the Vulnerability clicked?
- If not, is there a possibility to somehow mask the VulnerabilityId so it simple shows a specific word (e.g. "Details") and on click the token is set to the actual value in the cell?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi gbhw,
use values(...):
| stats values(Vulnerability) AS Vulnerabilities values(VulnerabilityId) AS VulnerabilityId by IP
But beware because the display order of Vulnerabilities and VulnerabilityId isn't the same for both the lists, in other words Vulnerabilities and VulnerabilityId are orders in alphabetical order and it could possible that thefirst Vulnerability isn't related to the first VulnerabilityId.
If you want you could have a different approach:
you could use the Vulnerability description as key, or you could correlate Vulnerability and VulnerabilityId before stats and after stats use a regex to extract VulnerabilityId to use for drilldown, in other words:
| eval column=Vulnerability."_".VulnerabilityId
| stats values(column) AS Vulnerabilities by IP
| rex field=column "[^_]*_(?<VulnerabilityId>.*)"
| table IP Vulnerabilities VulnerabilityId
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi gbhw,
use values(...):
| stats values(Vulnerability) AS Vulnerabilities values(VulnerabilityId) AS VulnerabilityId by IP
But beware because the display order of Vulnerabilities and VulnerabilityId isn't the same for both the lists, in other words Vulnerabilities and VulnerabilityId are orders in alphabetical order and it could possible that thefirst Vulnerability isn't related to the first VulnerabilityId.
If you want you could have a different approach:
you could use the Vulnerability description as key, or you could correlate Vulnerability and VulnerabilityId before stats and after stats use a regex to extract VulnerabilityId to use for drilldown, in other words:
| eval column=Vulnerability."_".VulnerabilityId
| stats values(column) AS Vulnerabilities by IP
| rex field=column "[^_]*_(?<VulnerabilityId>.*)"
| table IP Vulnerabilities VulnerabilityId
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I tried your suggestion using the values instead of list but it has the same behavior.
But the idea of using a combined value and extract the Id from it is a good workaround. I've tested it and it works.
Thank you!!