- Apps & Add-ons
- :
- Splunk Development
- :
- Splunk Dev
- :
- Re: The issue is that we have so many windows auth...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The issue is that we have so many windows authentication failures after creating Authentication Data model
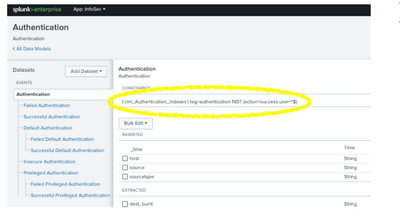
I created an Authentication data model that has default, Insecure, and Priviledge Authentication Data model. It also uses action=success and action=failures. Please see screenshot below:
I can see the data coming in from different sources but the issue is that we have so many windows authentication failures. Please how can I fix this configurations issues? Has anybody come across such issues?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Are you sure this is a Splunk issue? Is it possible Splunk has just pointed out a problem that already exists in your company?
If you built the datamodel yourself, double-check the logic.
To properly diagnose authentication failures, we need to see the constraint for the Failed Authentication dataset.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
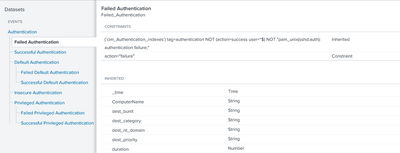
The constraints for the Failed Authenication Data model is:
I have another question. How can I review the event codes that are failing for windows authentication failures?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm confused. The Failed Authentication dataset inherits a condition ('NOT "pam_unix(sshd:auth): authentication failure;"') that is not shown in the screenshot of the parent data set in the OP.
I don't understand the new question, either, but new questions usually warrant new postings.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
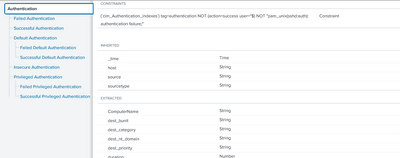
Pardon me. The parent screenshot I shared before was the wrong one. Below is actually the screenshot of the parent dataset:
Please let me know.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Take the constraint from the dataset and run it in a search window. Verify the results are as expected. Modify the query as necessary to get the desired results then update the datamodel.
If this reply helps you, Karma would be appreciated.