Are you a member of the Splunk Community?
- Find Answers
- :
- Splunk Administration
- :
- Admin Other
- :
- Knowledge Management
- :
- In Windows Security logs while using transaction w...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
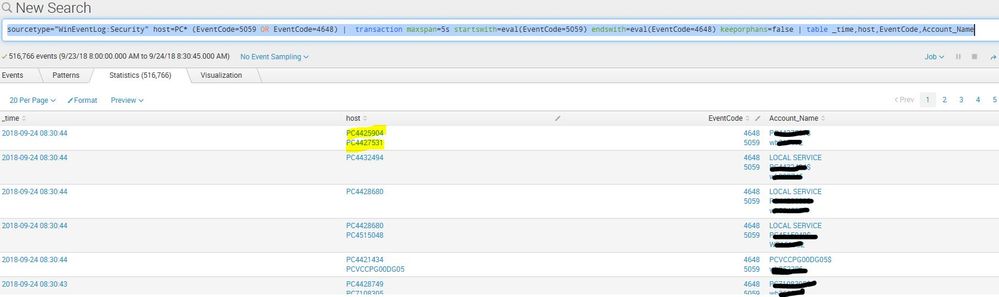
sourcetype="WinEventLog:Security" host=PC* (EventCode=5059 OR EventCode=4648) | transaction maxspan=5s startswith=eval(EventCode=5059) endswith=eval(EventCode=4648) keeporphans=false | table _time,host,EventCode,Account_Name
I'm trying to query for all computers and find the event code 5059 followed with an event 4648 within 5 seconds from the same computer. However, the search results return events from 2 different computers and matches them to the same transaction. How can I improve this search query?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It may be the only thing you are actually missing is the field list to match on.
sourcetype="WinEventLog:Security" host=PC* (EventCode=5059 OR EventCode=4648)
| transaction maxspan=5s startswith=eval(EventCode=5059) endswith=eval(EventCode=4648) keeporphans=false host
| table _time,host,EventCode,Account_Name
Add that host to the end of the transaction says to only connect them on where host is the same.
Happy Splunking!
-Rich
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It may be the only thing you are actually missing is the field list to match on.
sourcetype="WinEventLog:Security" host=PC* (EventCode=5059 OR EventCode=4648)
| transaction maxspan=5s startswith=eval(EventCode=5059) endswith=eval(EventCode=4648) keeporphans=false host
| table _time,host,EventCode,Account_Name
Add that host to the end of the transaction says to only connect them on where host is the same.
Happy Splunking!
-Rich
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is there any way to add 3 or more consecutive events to the transacation? I see only start and end, meaning only 2 events?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If there were three or more consecutive events, they would all be added in. You can possibly see this already if you check the field "eventcount".
OH! I see why. Sorry, I wasn't paying close enough attention.
In the initial search, you search ONLY for (EventCode=5059 OR EventCode=4648). So that's all you get. And if you then build a transaction starting with 5059 and ending with 4648...
Try removing that bit.
sourcetype="WinEventLog:Security" host=PC*
| transaction maxspan=5s startswith=eval(EventCode=5059) endswith=eval(EventCode=4648) keeporphans=false host
| table _time,host,EventCode,Account_Name
Let me know if that's better. 🙂
-Rich