Join the Conversation
- Find Answers
- :
- Splunk Administration
- :
- Admin Other
- :
- Installation
- :
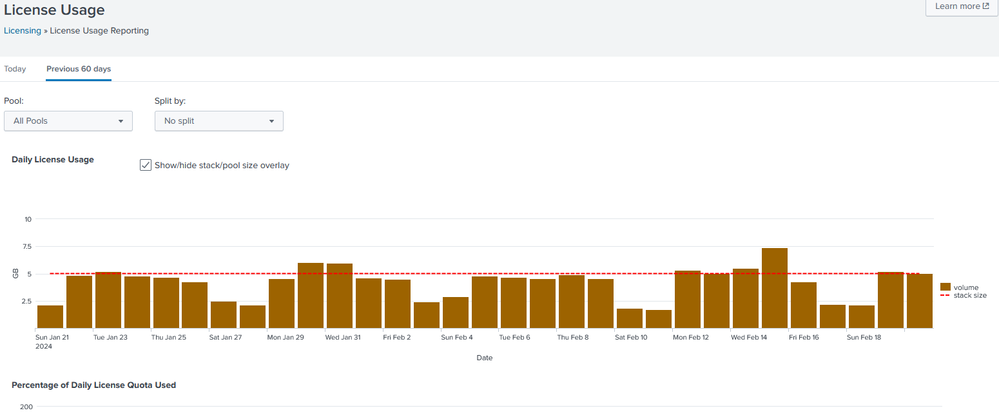
- Splunk License Report - Previous 60 days - Charts ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi
In the Splunk's License Usage Report, for the "Previous 60 days", the two first charts "Daily License Usage" and "Percentage of Daily License Quota Used" have only 31 columns - instead of the expected 60.
Splunk version is 9.0.41
Just wanted to report
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank You very much @gcusello
OK that I go for _internal retention from 30 to 60 days.
But when I open - "Open In Search" - the two first dashboards, the code is as below
Daily License Usage
index=_internal [`set_local_host`] source=*license_usage.log* type="RolloverSummary" earliest=-30d@d | eval _time=_time - 43200 | bin _time span=1d | stats latest(b) AS b by slave, pool, _time | timechart span=1d sum(b) AS "volume" fixedrange=false | join type=outer _time [search index=_internal [`set_local_host`] source=*license_usage.log* type="RolloverSummary" earliest=-30d@d | eval _time=_time - 43200 | bin _time span=1d | dedup _time stack | stats sum(stacksz) AS "stack size" by _time] | fields - _timediff | foreach * [eval <<FIELD>>=round('<<FIELD>>'/1024/1024/1024, 3)]
Percentage of Daily License Quota Used
index=_internal [`set_local_host`] source=*license_usage.log* type="RolloverSummary" earliest=-30d@d | eval _time=_time - 43200 | bin _time span=1d | stats latest(b) AS b latest(stacksz) AS stacksz by slave, pool, _time | stats sum(b) AS volumeB max(stacksz) AS stacksz by _time | eval pctused=round(volumeB/stacksz*100,2) | timechart span=1d max(pctused) AS "% used" fixedrange=false
As you see, there are " earliest=-30d@d" in both of them, two in the first dashboard and one in the second.
I guess I need to set those to " earliest=-60d@d".
Otherwise, extending the retention to 60 days, would have any value ?
best regards
Altin
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Further more, if I "open In search" the search code of the two dashboards, and change every occurrence of -30d@d to -60d@d, and search, there will be 60 bars - last 60 days.
This happens although the frozenTimePeriodInSec = 2592000 (30 days) for index _internal.
Do we really need to double this setting?
It looks that just changing -30d@d to -60d@d, is enough.
best regards
Altin
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I can have the result with 60 days without changing index retention. I do not know why.
But I have to change the -30 days to -60 days in Splunk-owned form that does not allow editing.
Guess I will keep this in mind and see if Splunk will change any thing in the coming versions.
best regards
Altin
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
But this form has no Edit button.
Which means it is not meant to be modified other then by Splunk itself.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I do have data on my _internal index for much longer then. At least from sourcetype splunkd
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @altink ,
retention is defined at index level, so you cannot have a different retention for a sourcetype.
If you didn't modified the retention of this index ,by default it's 30 days and ususlly is reducted to save disk space.
See in the Monitoring Console or in [Settings > index] what's the latest event in your _internal index to understand the retention of your _internal index and eventually enlarge it changing the frozenTimePeriodInSecs parametr in $SPLUNK_HOME/etc/system/local/indexes.conf file _internal stanza.
If you didn't modified this file before you haven't it in the local folder, so you have to copy the stand from the same file in the default folder.
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is it a problem if I modify it directly under the defaul folder?
Is a restart needed after ?
best regards
Altin
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @altink ,
never modify something in the default folder!
at the first upgrade you'll loose every changes.
copy the entire file or only the stanza to modify in the local folder and modify the value.
At the end, restart Splunk.
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is a Splunk's form, not mine, not of any third party app (be this Splunk supported).
If a label on a form says last 60 days, then the respective dashboards should be showing the last 60 days - ad not less.
Ps. at my _internal index there are data much earlier then 30 days. Ex. can search data from early November 2023. Didn't try earlier.
regards
Altin
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @altink ,
the issue isn't in the dashboard that's correct, the issue is on the Data retention that is less than 60 days.
If you want 60 days report,you have to enlarge the _internal retention.
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Try this Dashboard we do use.
Change this (2 places) host="your-license server" to name of your license server. If you have only one server or run the code on the license server, just remove the host="your-license server" complete. It will show on line red line that is your license limit and one bar graf that shows GB license use pr day. To get MB, just remove one /1024
<form version="1.1" theme="dark">
<label>Used License</label>
<fieldset submitButton="false">
<input type="time">
<label></label>
<default>
<earliest>-3mon</earliest>
<latest>now</latest>
</default>
</input>
</fieldset>
<row>
<panel>
<chart>
<search>
<query>
index=_telemetry host="your-license server" source=*license_usage_summary.log* type="RolloverSummary"
| eval _time=_time - 86400
| bin _time span=1d
| stats latest(b) AS b by slave, pool, _time
| timechart span=1d sum(b) AS "volume" fixedrange=false
| join type=outer _time
[ search index=_telemetry host="your-license server" source=*license_usage_summary.log* type="RolloverSummary"
| eval _time=_time - 86400
| bin _time span=1d
| dedup _time stack
| stats sum(stacksz) AS "Limit" by _time]
| fields - _timediff
| foreach "*"
[ eval <<FIELD>>=round('<<FIELD>>'/1024/1024/1024, 3)]</query>
</search>
<option name="charting.axisTitleX.visibility">collapsed</option>
<option name="charting.axisY.minimumNumber">0</option>
<option name="charting.chart">column</option>
<option name="charting.chart.overlayFields">"Limit"</option>
<option name="charting.drilldown">all</option>
<option name="charting.fieldDashStyles">{"Limit":"shortDash"}</option>
<option name="charting.seriesColors">[0x006D9C,0xFF0000]</option>
<option name="charting.lineWidth">4</option>
<option name="height">800</option>
</chart>
</panel>
</row>
</form>
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @altink,
it depends on the retention of your _internal data: if you want to have 60 days, you have to enlarge the retention of your _internal index.
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You should look at the _internal index size before changing it
| dbinspect index=_internal
| stats sum(sizeOnDiskMB)
In our setup with 30 days of internal index, size of file is 680GB. So double the time, double this file.
As you see above, I posted a dashboard uses _telemetry index instead to see index uses. Our telemetry index is 215 MB of size. We have change _telemetry to 20 years, since it does not take up much space:
[_telemetry]
# This is 20 years to get longer historical license useage.
frozenTimePeriodInSecs = 788400000
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content