- Splunk Answers
- :
- Splunk Administration
- :
- Installation
- :
- Re: Splunk Installation in CentOS
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
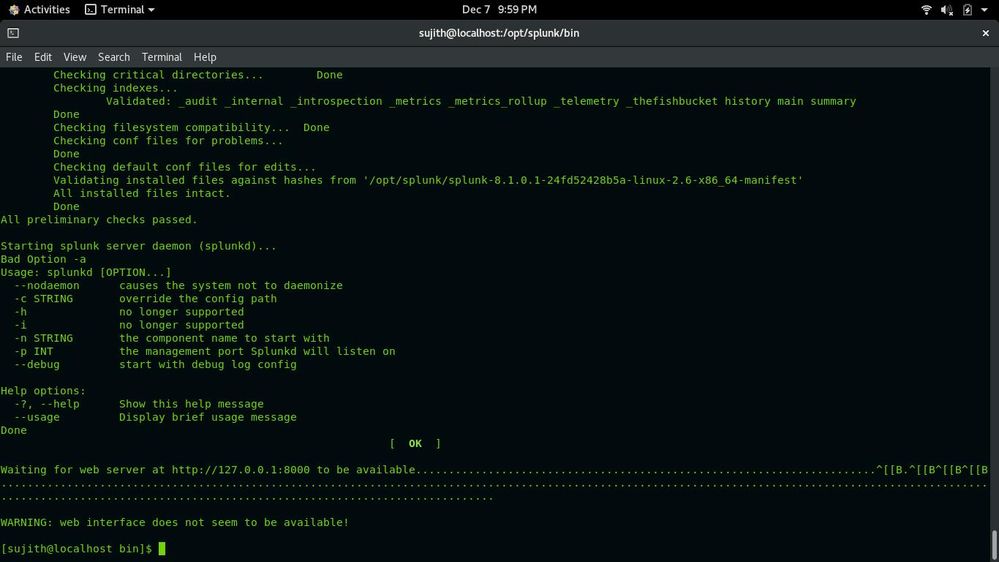
Hi all,
I am new to Splunk and I am unable to complete the installation in CentOS 8.
Error: Unable to start the web interface. (Reference image attached)
Please help.
Thanks in advance.
Best regards,
Sujith Thyagaraja
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you're using https://www.bitsioinc.com/tutorials/install-splunk-centos/ to install, they have a typo in the start command. It should be:
./splunk start --accept-licenseThey've only got 1 hyphen in the accept license, and it's trying to pass just -a to Splunk.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you're using https://www.bitsioinc.com/tutorials/install-splunk-centos/ to install, they have a typo in the start command. It should be:
./splunk start --accept-licenseThey've only got 1 hyphen in the accept license, and it's trying to pass just -a to Splunk.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Sorry I can't reproduce the error with the provided informations.
How do you install Splunk Enterprise? Because the official Packages shouldn't try to start splunkd with a "bad option".
From source package the installation runes without any problem. Also when I remove the user-seed.conf part. Tested on vagrant with a Centos 8.2.
Here the Vagrantfile example… with shell provisioning.
# -*- mode: ruby -*-
# vi: set ft=ruby :
Vagrant.configure("2") do |config|
config.vm.define "splunkserver" do |server|
server.vm.box = "bento/centos-8.2"
server.vm.box_check_update = false
server.vm.network "private_network", ip: "192.168.130.182"
server.vm.provision "shell", inline: <<-SHELL
hostname "testsplunkserver"
yum install wget -y
useradd -m -d /opt/splunk splunk
wget -O /opt/splunk/$(curl -s https://www.splunk.com/en_us/download/splunk-enterprise.html | grep -o "data-link[^ ]* " | grep "Linux" | sed "s\/data-link=\\"\/\/;s\/\\"\/\/" | sed "s\/.*\\/\/\/") $(curl -s https://www.splunk.com/en_us/download/splunk-enterprise.html | grep -o "data-link[^ ]* " | grep "Linux" | sed "s\/data-link=\\"\/\/;s\/\\"\/\/")
echo "file=\\$\(ls /opt/splunk/\*.tgz\)
mkdir \\$\{file%.tgz\}
tar xvzf \\$file --strip-components 1 -C \\$\{file%.tgz\}
ln -s \\$\{file%.tgz\} /opt/splunk/current
echo \\"\[user_info\]
USERNAME = admin
PASSWORD = changeme\\" \>\> /opt/splunk/current/etc/system/local/user-seed.conf
echo \\"SPLUNK_WEB_NAME=splunkweb
SPLUNK_HOME=/opt/splunk/current
SPLUNK_SERVER_NAME=Splunkd
SPLUNK_OS_USER=splunk\\" \>\> /opt/splunk/current/etc/splunk-launch.conf
/opt/splunk/current/bin/splunk start --accept-license --answer-yes --no-prompt
rm -f \\$file" >> /opt/splunk/splunk_install.sh
chown splunk:splunk /opt/splunk/splunk*
chmod 766 /opt/splunk/splunk_install.sh
sudo -u splunk /opt/splunk/splunk_install.sh
echo "# .bash_profile
# Get the aliases and functions
if [ -f ~/.bashrc ]; then
. ~/.bashrc
fi
# User specific environment and startup programs
PATH=\\$PATH:\\$HOME/.local/bin:\\$HOME/bin:\\$HOME/current/bin
export PATH" > /opt/splunk/.bash_profile
/opt/splunk/current/bin/splunk enable boot-start -user splunk
SHELL
end
end
Video of a vagrant up without user-seed.conf
https://youtu.be/VO_r8JX4Su0
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Did you try connecting to the web interface? I've had the same message appear in the CLI and was still able to use the GUI.
If this reply helps you, Karma would be appreciated.