- Find Answers
- :
- Splunk Administration
- :
- Getting Data In
- :
- Re: Use foreach, inputlookup, subsearch and index
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Use foreach, inputlookup, subsearch and index
Hi Splunkers.
I've been trying for weeks to do the following:
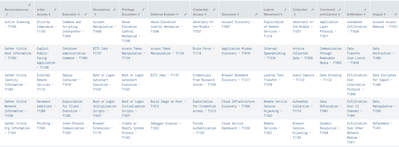
I have a search that outputs a table with MITRE techniques as shown below:
Query
index=notable search_name="Endpoint - KTH*"
| fields tactic_mitre, technique_mitre, risk_mitre, src_user, user, Computer, dest, search_name
| stats count by technique_mitre
|eval codes_tech=technique_mitre
|makemv delim=", " codes_tech
|mvexpand codes_tech
|rename count as carry
|stats sum(carry) as Total by codes_tech
Result
And I have another query that brings me a table with the IDs and names of the Techniques and tactics of MITRE
Query
| inputlookup mitre_lookup
| foreach TA00*
[| lookup mitre_tt_lookup technique_id as <<FIELD>> OUTPUT technique_name as <<FIELD>>_technique_name
| eval <<FIELD>>_technique_name=mvindex(<<FIELD>>_technique_name, 0)
| eval <<FIELD>>=<<FIELD>>_technique_name . " - " . <<FIELD>>]
| fields TA0043,TA0001, TA0002, TA0003, TA0004, TA0005, TA0006, TA0007, TA0008, TA0009, TA0011, TA0010, TA0040, TA0042
| rename TA0043 as "Reconnaissance", TA0042 as "Resource Development", TA0001 as "Initial Access", TA0002 as "Execution", TA0003 as "Persistence", TA0004 as "Privilege Escalation", TA0005 as "Defense Evasion", TA0006 as "Credential Access", TA0007 as "Discovery", TA0008 as "Lateral Movement", TA0009 as "Collection", TA0011 as "Command and Control", TA0010 as "Exfiltration", TA0040 as "Impact"
Result
I would like to search within the MITRE table for the codes_tech of the first query and if Total is greater than 0 I would put the Total and otherwise leave the other IDs at 0
Please, I really need your help, please, please, please...
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
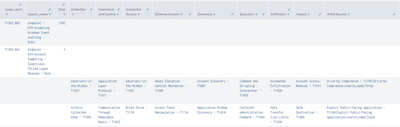
Merge the queries, but it shows me the following
The query is as follows:
index=notable search_name="Endpoint - KTH*"
| fields tactic_mitre, technique_mitre, search_name
| stats count by technique_mitre, search_name
|eval codes_tech=technique_mitre
|makemv delim=", " codes_tech
|mvexpand codes_tech
|rename count as carry
|stats values(search_name) as search_name, sum(carry) as Total by codes_tech
|append [| inputlookup mitre_lookup
| foreach TA00*
[| lookup mitre_tt_lookup technique_id as <<FIELD>> OUTPUT technique_name as <<FIELD>>_technique_name
| eval <<FIELD>>_technique_name=mvindex(<<FIELD>>_technique_name, 0)
| eval <<FIELD>>=<<FIELD>>_technique_name . " - " . <<FIELD>>]
| join type=left codes_tech
[
| rename technique_id as TA0001, search_name as TA0001_rule_name_list, Total as TA0001_max_score ]
| fillnull value=search_name TA0001,TA0001_rule_name_list,TA0001_technique_name
| fillnull value=Total TA0001_attack_count,TA0001_max_score
| eval TA0001=TA0001."|".TA0001_technique_name."|".TA0001_rule_name_list."|".TA0001_max_score
| join type=left codes_tech
[
| rename technique_id as TA0003, search_name as TA0003_rule_name_list, Total as TA0003_max_score ]
| fillnull value=search_name TA0003,TA0003_rule_name_list,TA0003_technique_name
| fillnull value=Total TA0003_attack_count,TA0003_max_score
| eval TA0003=TA0003."|".TA0003_technique_name."|".TA0003_rule_name_list."|".TA0003_max_score]
| rename TA0043 as "Reconnaissance", TA0042 as "Resource Development", TA0001 as "Initial Access", TA0002 as "Execution", TA0003 as "Persistence", TA0004 as "Privilege Escalation", TA0005 as "Defense Evasion", TA0006 as "Credential Access", TA0007 as "Discovery", TA0008 as "Lateral Movement", TA0009 as "Collection", TA0011 as "Command and Control", TA0010 as "Exfiltration", TA0040 as "Impact"
I want the codes_tech data to look for it in the tactics columns and when it finds the codes_tech ID, put the value of search_name and total