- Splunk Answers
- :
- Using Splunk
- :
- Alerting
- :
- Re: windows user ending in $
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
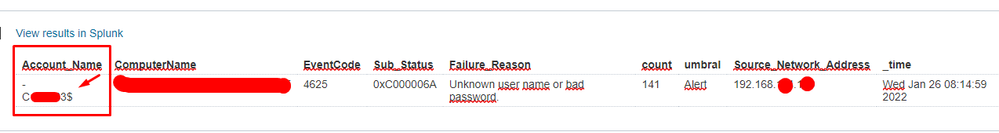
I have created a windows level brute force attack alert to alert me when X number of authentication failures occur in a 15 min interval.
sometimes I see an alert where the user is the same hostname but ends in the $ sign
I have searched the windows documentation but it is not completely clear to me, could someone give me their opinion on what it is, if it is relevant or a false positive.
tnx
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As there are divided opinions, I prefer that it be the client who decides
thanks to all
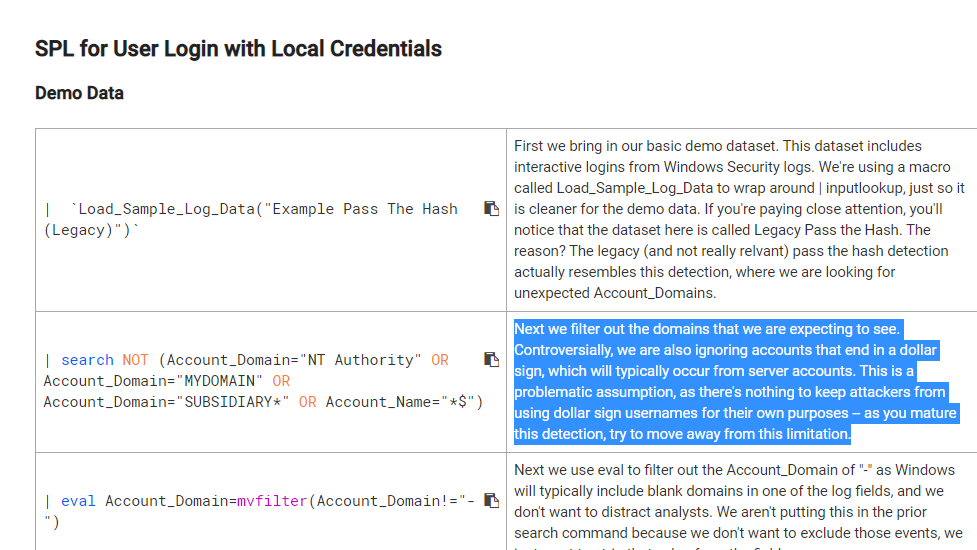
"Next we filter out the domains that we are expecting to see. Controversially, we are also ignoring accounts that end in a dollar sign, which will typically occur from server accounts. This is a problematic assumption, as there's nothing to keep attackers from using dollar sign usernames for their own purposes -- as you mature this detection, try to move away from this limitation."
https://docs.splunksecurityessentials.com/content-detail/user_login_local_credentials/
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As there are divided opinions, I prefer that it be the client who decides
thanks to all
"Next we filter out the domains that we are expecting to see. Controversially, we are also ignoring accounts that end in a dollar sign, which will typically occur from server accounts. This is a problematic assumption, as there's nothing to keep attackers from using dollar sign usernames for their own purposes -- as you mature this detection, try to move away from this limitation."
https://docs.splunksecurityessentials.com/content-detail/user_login_local_credentials/
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In AD computer accounts end with dollar sign. So you probably have your computers named after primary users.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Or those could be a managed service accounts https://docs.microsoft.com/en-us/windows-server/security/group-managed-service-accounts/group-manage...
In that case you probably should check those?
r. Ismo
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
AIUI, names ending with $ are system accounts and can be ignored.
If this reply helps you, Karma would be appreciated.