- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- search field from 1 index to other index field
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi ,
i have a index "otx" and having field "indicator" so i want to trigger alert if any IP address from "indicator" match to my ASA firewall logs where "dest_ip" is field in ASA logs. i am trying belong query.
index=asa | join dest_ip [search sourcetype="otx:indicator" type=IPV4 | fields indicator | rename indicator as dest_ip]
Thanks
shashi
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @shashilendra,
Please try below, result should show timestamp of the last asa events with src_ip values for matching dest_ip.
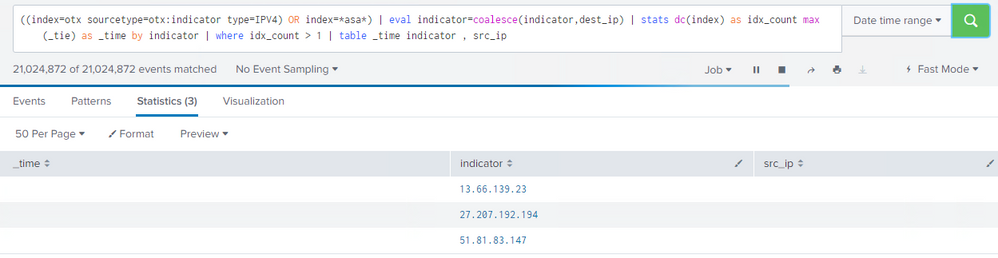
((index=otx sourcetype=otx:indicator type=IPV4) OR index=*asa*)
| eval indicator=coalesce(indicator,dest_ip)
| eval asa_time=if(index=="*asa*",_time,0)
| stats dc(index) as idx_count max(asa_time) as _time values(src_ip) as src_ip by indicator
| where idx_count > 1
| table _time src_ip indicator
If this reply helps you an upvote appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
(sourcetype="otx:indicator" type=IPV4) OR (index=*asa* sorceytpe="cisco:asa" dest_ip=*)
| eval ip=coalesce(indicator,dest_ip)
| stats min(_time) as first_time max(_time) last_time range(_time) as durtion values(title) as title by ip
| convert ctime(first_time) ctime(last_time)
| search title=*
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @shashilendra,
Please try below, result should show timestamp of the last asa events with src_ip values for matching dest_ip.
((index=otx sourcetype=otx:indicator type=IPV4) OR index=*asa*)
| eval indicator=coalesce(indicator,dest_ip)
| eval asa_time=if(index=="*asa*",_time,0)
| stats dc(index) as idx_count max(asa_time) as _time values(src_ip) as src_ip by indicator
| where idx_count > 1
| table _time src_ip indicator
If this reply helps you an upvote appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @shashilendra,
Sorry, where command was wrong on my search, please try below;
((index=otx sourcetype=otx:indicator type=IPV4) OR index=*asa*)
| eval indicator=coalesce(indicator,dest_ip)
| stats dc(index) as idx_count max(_time) as _time by indicator
| where idx_count > 1
| table _time indicator- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi ,
i can see the matching IP address from both index , but i want to know which source IP address Triger this traffic and at what time . in ASA log "src_ip" field contain the source IP address.
i will create a alert which contain time src ip , dest_ip/indicator
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @shashilendra,
Please try below, you can adapt to your need;
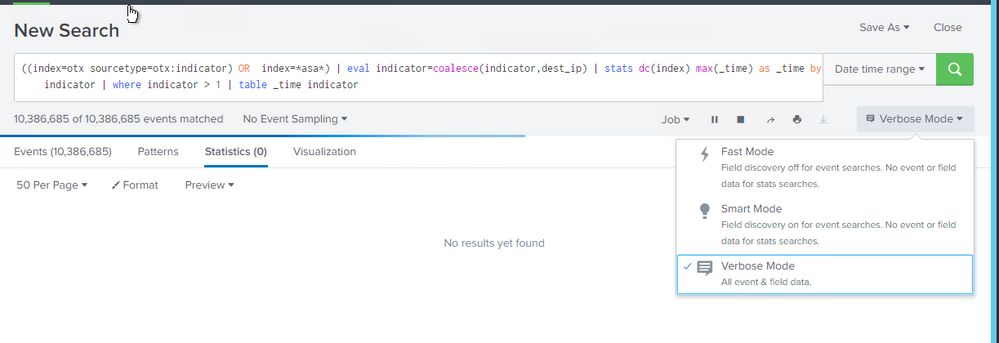
((index=otx sourcetype=otx:indicator) OR index=asa)
| eval indicator=coalesce(indicator,dest_ip)
| stats dc(index) max(_time) as _time by indicator
| where indicator > 1
| table _time indicator
If this reply helps you an upvote is appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
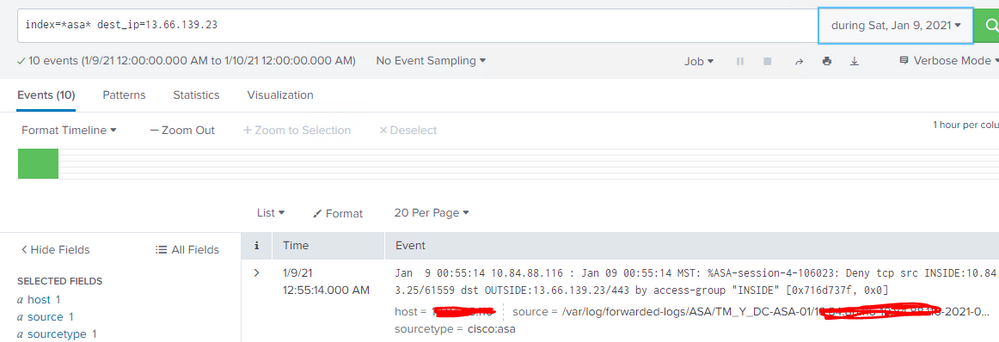
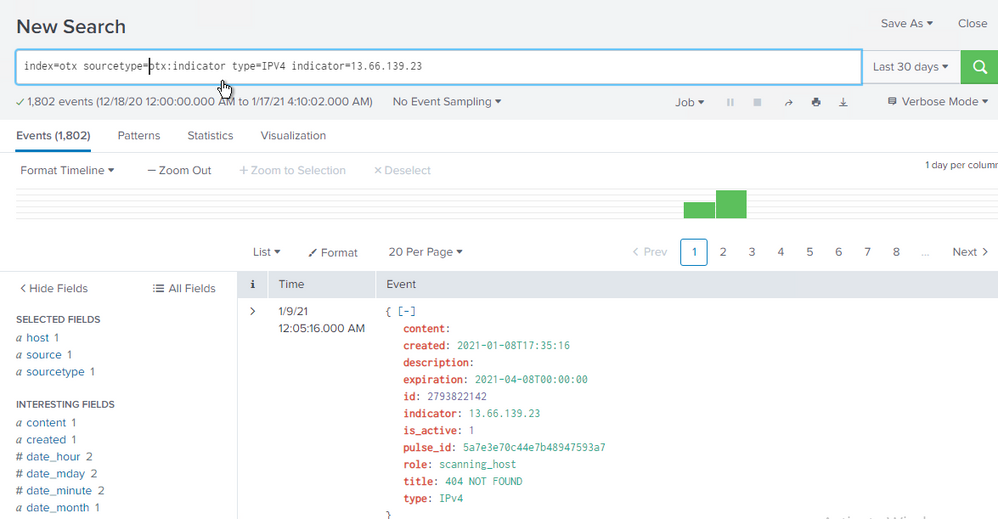
Hi ,
i tried your query but no result , however both index having matching IP address.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Even i tried below query as well
index=asa dest_ip=* [search sourcetype="otx:indicator" type=IPV4 | fields indicator | rename indicator as dest_ip] | table dest_ip
Thanks
shashi