Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Splunk Search
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- need search with if condition
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
avikc100
Path Finder
06-08-2021
09:02 PM
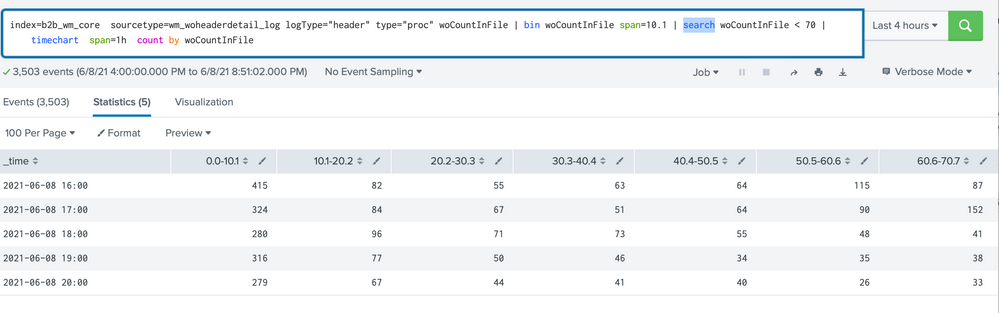
Am getting data in this format now.
but i need to show only those row where sum of all column values are > 500
am trying somethign like this. am new so unable to form the query, please help
index=b2b_wm_core sourcetype=wm_woheaderdetail_log logType="header" type="proc" woCountInFile | bin woCountInFile span=10.1 |
search if(count(woCountInFile < 70) > 500) | timechart span=1h count by woCountInFile
1 Solution
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
avikc100
Path Finder
06-08-2021
10:45 PM
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
avikc100
Path Finder
06-08-2021
10:45 PM
its working now! Appreciate!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
bowesmana

SplunkTrust
06-08-2021
10:20 PM
If the existing columns are what you initial expect before your >500 test, then simply add the following to the end of your query
| addtotals
| where Total>500
| fields - Total
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
bowesmana

SplunkTrust
06-09-2021
01:31 AM
If it works for you, please mark the question as solved, so others can benefit
Get Updates on the Splunk Community!
Introducing the 2024 SplunkTrust!
Hello, Splunk Community! We are beyond thrilled to announce our newest group of SplunkTrust members!
The ...
Introducing the 2024 Splunk MVPs!
We are excited to announce the 2024 cohort of the Splunk MVP program. Splunk MVPs are passionate members of ...
Splunk Custom Visualizations App End of Life
The Splunk Custom Visualizations apps End of Life for SimpleXML will reach end of support on Dec 21, 2024, ...