- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: json field extraction to be used for calculati...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
Recently I added a question about how I could extract fields or get a table from a json input (https://community.splunk.com/t5/Splunk-Search/Field-extraction/m-p/517524#M145531). The solution was provided in one of the responses being:
index=_internal | head 1
| eval _raw = "[{\"Type\":\"Attention\",\"ABUSE\":18,\"GSD 24x7\":1,\"CLOUD\":0,\"DC\":0,\"ECL\":0,\"ITMS\":0,\"NET\":0,\"RFO\":17,\"Total\":36},{\"Type\":\"Active\",\"ABUSE\":0,\"GSD 24x7\":22,\"CLOUD\":38,\"DC\":5,\"ECL\":1,\"ITMS\":0,\"NET\":12,\"RFO\":2,\"Total\":80},{\"Type\":\"Total\",\"ABUSE\":18,\"GSD 24x7\":23,\"CLOUD\":38,\"DC\":5,\"ECL\":1,\"ITMS\":0,\"NET\":12,\"RFO\":19,\"Total\":116},{\"Type\":\"P1\",\"ABUSE\":0,\"GSD 24x7\":0,\"CLOUD\":0,\"DC\":0,\"ECL\":0,\"ITMS\":0,\"NET\":0,\"RFO\":6,\"Total\":6},{\"Type\":\"P2\",\"ABUSE\":0,\"GSD 24x7\":1,\"CLOUD\":0,\"DC\":0,\"ECL\":0,\"ITMS\":0,\"NET\":0,\"RFO\":10,\"Total\":11},{\"Type\":\"P3\/4\",\"ABUSE\":18,\"GSD 24x7\":0,\"CLOUD\":0,\"DC\":0,\"ECL\":0,\"ITMS\":0,\"NET\":0,\"RFO\":1,\"Total\":19}]"
| rename COMMENTS AS "Previous lines generate your sample data, you get it by indes=xxx"
| spath
| rename {}.* as json_*
| table json_*
(Thank you @isoutamo ).
Now I have a new request for this. I have the table but I would like to add some stats to the numbers. This information is related to the shifts we have in rotation and I would like to add for example, a simple difference between how much events there were at the beginning and at the end of the shift. The issue is that even with the table, the fields are not exactly fields I can filter.
Any ideas?
Thank you in advance!
PD: this is the raw data:
<
>[{"Type":"Attention","ABUSE":6,"GSD 24x7":3,"CLOUD":1,"DC":0,"ECL":0,"ITMS":0,"NET":0,"RFO":15,"Total":25},{"Type":"Active","ABUSE":0,"GSD 24x7":12,"CLOUD":44,"DC":9,"ECL":2,"ITMS":0,"NET":13,"RFO":1,"Total":81},{"Type":"Total","ABUSE":6,"GSD 24x7":15,"CLOUD":45,"DC":9,"ECL":2,"ITMS":0,"NET":13,"RFO":16,"Total":106},{"Type":"P1","ABUSE":0,"GSD 24x7":0,"CLOUD":0,"DC":0,"ECL":0,"ITMS":0,"NET":0,"RFO":6,"Total":6},{"Type":"P2","ABUSE":0,"GSD 24x7":1,"CLOUD":0,"DC":0,"ECL":0,"ITMS":0,"NET":0,"RFO":9,"Total":10},{"Type":"P3\/4","ABUSE":6,"GSD 24x7":2,"CLOUD":1,"DC":0,"ECL":0,"ITMS":0,"NET":0,"RFO":0,"Total":9}]
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
| spath {} output=root |mvexpand root |spath input=root |stats as_you_like
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
| spath {} output=root |mvexpand root |spath input=root |stats as_you_like
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
This works, but I just have onw value for the "type" field, and I would like to select between the "Attention", "Active" and priorities, which is all included in the that field.
Any clue on how to improve this part?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
...| table type | search type ="as_you_like"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
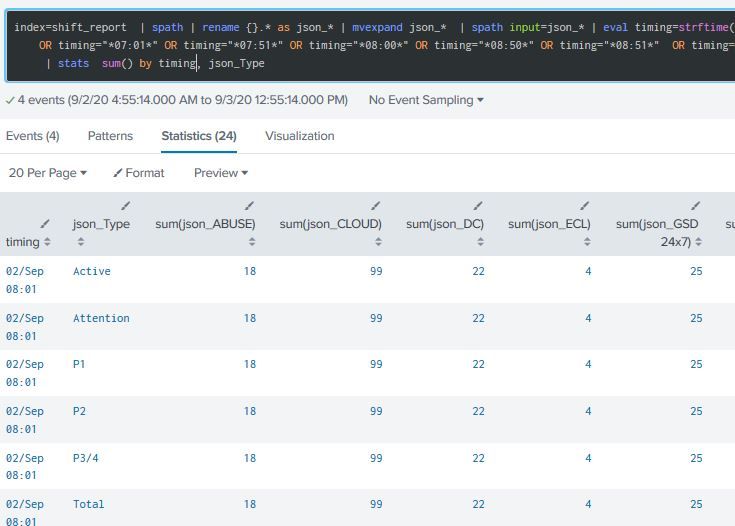
It seems he's not recognizing the field json_Type, or at least its values.
For the picture you can see the sum values are the same for all the rows