- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How to use the condition stanza in this spl query...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to use the condition stanza in this spl query?
Hi, I'm trying to find the alerts by user between the period of 2 hours like Alert1,Alert2 Here I need a spl query for this condition
* And one more condition spl is In bwtween 2hours if there is an alert for single user more than 3 times it should raise an alert.
Thanks.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What have you tried so far and what results did you get?
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
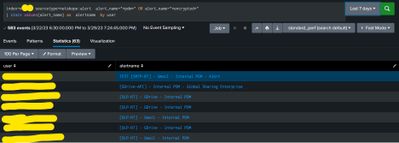
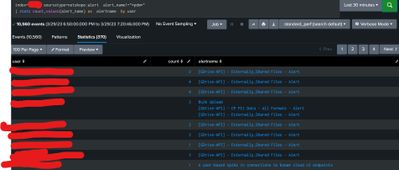
Please have a look on usecase snapshot once.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@richgalloway
Hi,
Use case :1
If the user triggers pdm and encrypt alerts both in a period of 2 hours it should raise an alert.
Use case:2
If the user triggers other than pdm in between 2 hours for single user more than 3 times it should raise an alert .
Thanks
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You have the searches so what is preventing you from saving them as alerts? Click "Save as" in the top-right corner of the search to make it into an alert.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
My aim is creating a correlation search..
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In Enterprise Security, go to Configure->Content->Content Management then click the "Create New Content" button and select Correlation Search. Copy-and-paste your search from the S&R window into the Search box of the CS. Complete the rest of the CS form and click Save.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@richgalloway
what I'm trying to do is like
usecase1: alert_name!="*pdm*" by user
base search
--------------
| eval non_pdm_alert=if(alert_name!="*pdm*", 1, 0)
| sort _time
| streamstats count(non_pdm_alert) AS non_pdm_count by user time_window=2h
| where non_pdm_count>2
It is not giving desired output.
usecase 2: (alert_name="*PDM*" AND alert_name="*encrypted*")
base search
| eval both_alerts_triggered=if(alert_name="*pdm*" AND alert_name="*encrypted*", 1, 0)
| sort _time
| streamstats count(eval(both_alerts_triggered=1)) AS triggered_count by user time_window=2h
| where triggered_count>=2
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm uncertain about what the ask. First you asked for alerts. Then you shared your searches and asked how to make them into correlation searches. Now you share more searches and say the output is not what is desired. Just what is desired? How are the existing searches not meeting expectations? What are those expectations?
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi ,
My ask is if the user triggers both the alerts i.e pdm and encrypted with in a span of 2 hours.
Other one is if the user triggers non pdm alerts with in a span of 2 hours is my requirement
Please edit the above search as per the usecase.
Thanks
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Alerts are independent. There is no test for triggering more than one alert (unless you're using Enterprise Security). One alert would have to test for both (or more) conditions and trigger if all are met.
If this reply helps you, Karma would be appreciated.