- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- [help]Get the time duration within a specific sta...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
[help]Get the time duration within a specific start and end value?
Hi team,
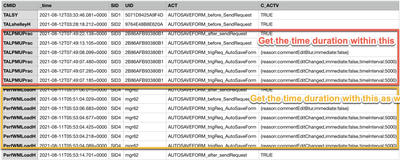
I have below data in splunk.
And I want to get the time duration when below range.
ACT start with "AUTOSAVEFORM_trigReq_AutoSaveForm", and end with "AUTOSAVEFORM_after_sendReques"
I have tried below queries , but it doesn;t return the correct result.
index=*bizx_application AND sourcetype=perf_log_bizx AND PID="PM_REVIEW" AND PLV=EVENT AND ACT="AUTOSAVEFORM_*" AND C_ACTV="*commentEdit*" OR ACT="*SendRequest"
|reverse
| transaction CMID SID UID startswith="AUTOSAVEFORM_trigReq_AutoSaveForm" endswith="AUTOSAVEFORM_after_sendRequest"
| table _time duration eventcount
Can anyone pease help provide a solution?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
i get expected result by below query:
index=*bizx_application AND sourcetype=perf_log_bizx AND PID="PM_REVIEW" AND PLV=EVENT AND ACT="AUTOSAVEFORM_*" AND C_ACTV="*commentEdit*" OR ACT="*SendRequest"
| sort _time CMID SID UID
| streamstats count(eval(ACT=="AUTOSAVEFORM_trigReq_AutoSaveForm")) as eventCounter by CMID SID UID ACT C_ACTV reset_after="ACT=AUTOSAVEFORM_trigReq_AutoSaveForm" reset_on_change=true
| table SN, CMN,CMID, CIP, _time, SID,UID, ACT, C_ACTV,eventCounter
| eval ACT=if(ACT=="AUTOSAVEFORM_trigReq_AutoSaveForm" AND C_ACTV=="{reason:commentEditChanged,immediate:false,timeInterval:5000}", ACT+eventCounter, ACT)
| sort - _time CMID SID UID
| transaction CMID SID UID startswith="ACT=AUTOSAVEFORM_trigReq_AutoSaveForm1" endswith="ACT=AUTOSAVEFORM_after_sendRequest"
| table _time CMN duration
| chart list(duration) as interval by _time, CMN
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hi @cheriemilk,
You need to provide an eval/search expression to the startswith and endwith arguments.
index=*bizx_application AND sourcetype=perf_log_bizx AND PID="PM_REVIEW" AND PLV=EVENT AND ACT="AUTOSAVEFORM_*" AND C_ACTV="*commentEdit*" OR ACT="*SendRequest"
| sort - _time, CMID, SID, UID
| transaction CMID SID UID startswith="ACT=AUTOSAVEFORM_trigReq_AutoSaveForm" endswith="ACT=AUTOSAVEFORM_after_sendRequest"
| table _time duration eventcountMore details on here: https://docs.splunk.com/Documentation/Splunk/latest/SearchReference/Transaction#Filter_string_option...
If this reply helps you, a like would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @manjunathmeti ,
Thank you for the solution. But I am wondering if the result based on your suggested query is right or not?
The obvious problematic data is for 'eventcount'. In my screenshot->the transaction blocked with red, there're 6 events totally, but the query result shows this transaction only has 3 events for eventcount field. Is this correct? Looks like, the transaction doesn't start with the first 'ACT=AUTOSAVEFORM_trigReq_AutoSaveForm'.
Thanks,
Cherie