Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Splunk Search
×
Join the Conversation
Without signing in, you're just watching from the sidelines. Sign in or Register to connect, share, and be part of the Splunk Community.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: exclude results near a match (ie exclude match...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
exclude results near a match (ie exclude match AND +- 2 seconds)
spunk311z
Path Finder
03-22-2020
12:00 PM
I cant imagine this is possible, but splunk continuously surprises me, so ill ask:
Is there anyway to exclude results, from the same host, + or - 2 seconds from a match.
(or N seconds/minutes)
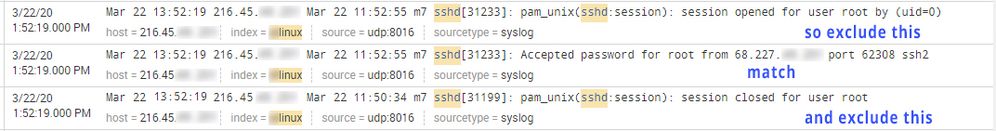
example, in this image below, id like to exclude the results above and below the match on the ip address 68.x.x.x ?
(this is just an example, i know i could get to my goal in this case by just showing IP matches, and investigating any IPs not on a known good IP lookup csv)
thanks
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
chinmoya
Communicator
03-22-2020
09:43 PM
You can use the bin command to group your data into your desired time-span and then do a distinct count on the ip.
Something like
index=_internal | bin _time span=5s | stats dc(clientip)
Get Updates on the Splunk Community!
Upcoming Webinar: Unmasking Insider Threats with Slunk Enterprise Security’s UEBA
Join us on Wed, Dec 10. at 10AM PST / 1PM EST for a live webinar and demo with Splunk experts! Discover how ...
.conf25 technical session recap of Observability for Gen AI: Monitoring LLM ...
If you’re unfamiliar, .conf is Splunk’s premier event where the Splunk community, customers, partners, and ...
A Season of Skills: New Splunk Courses to Light Up Your Learning Journey
There’s something special about this time of year—maybe it’s the glow of the holidays, maybe it’s the ...