- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Why is my search on JSON data producing duplicate ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
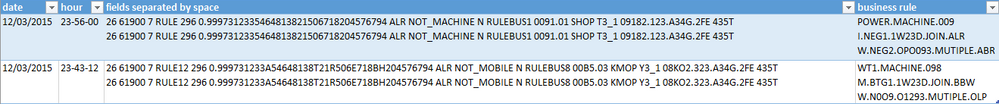
Hi guys,
I have a problem. Every time I try to run the following search, the result is duplicated in each line, but the date and time. What can be? My log is in format JSON.
index="my_index" source="my_source" sourcetype="my_sourcetype"
| rename field1 , field2, field3, ....
| eval Date = strftime(_time, "%d-%m-%Y")
| eval Hour = strftime(_time, "%H-%M-%S")
| spath output=Rules path=field.sub-field{}.code
| table Date, Hour, field1 , field2, field3, ....
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The data is most likely being indexed with indexed extractions and also searched with search-time extractions. Your indexer props.conf file likely has a line to do indexed extractions (not best practice):
INDEXED_EXTRACTIONS = json
On the search head props.conf:
KV_MODE = json
Deleting "INDEXED_EXTRACTIONS = json" from the indexer will solve the issue for everything indexed after the indexer is restarted. Anything already indexed will retain their indexed extractions, so you might want to delete the indexed data and re-index everything.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The data is most likely being indexed with indexed extractions and also searched with search-time extractions. Your indexer props.conf file likely has a line to do indexed extractions (not best practice):
INDEXED_EXTRACTIONS = json
On the search head props.conf:
KV_MODE = json
Deleting "INDEXED_EXTRACTIONS = json" from the indexer will solve the issue for everything indexed after the indexer is restarted. Anything already indexed will retain their indexed extractions, so you might want to delete the indexed data and re-index everything.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Or index the field and set KVMODE to none.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The other solution is to leave it as an indexed field and add KVMODE=false to the search head.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
landen,
This occurs every time that I try use the command table. I changed the configuration but continuous similarity. Do you have any ideia ?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The table command just accentuates the fact that the fields have multiple/duplicated values. If you do not use table and then click on the field in the left fields panel, you will see that it is also duplicated there, even though you are not using table. This answer is probably the correct explanation.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks guys. The solution works fine.