- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: Why is a value appearing twice in a table but ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
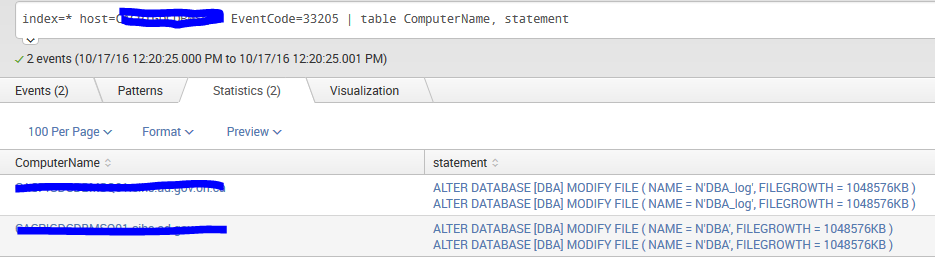
I'm running a very simple search to draw a table. One of the values returned is appearing twice in the table, but only occurs once in the event data. Is this a bug?
Here is the search string;
index=* host=serverhostname EventCode=33205 | table ComputerName, statement
The result in the table is the value for 'statement' appears twice. I get two events returned, with two lines each but only the 'statement' value is doubled. All other fields are blank on the second line.
Here is the event data that is being queried;
10/17/2016 12:20:25 PM
LogName=Application
SourceName=MSSQL$OTPMSSQL
EventCode=33205
EventType=0
Type=Information
ComputerName=HOSTNAME.FQDN
TaskCategory=None
OpCode=None
RecordNumber=904492
Keywords=Audit Success, Classic
Message=Audit event: event_time:2016-10-17 16:20:24.1512330
sequence_number:1
action_id:AL
succeeded:true
permission_bitmask:0
is_column_permission:false
session_id:136
server_principal_id:276
database_principal_id:1
target_server_principal_id:0
target_database_principal_id:0
object_id:8
class_type:DB
session_server_principal_name:DOMAIN\USERID
server_principal_name:DOMAIN\USERID
server_principal_sid:010500000000000515000000093a2a2426761e2f43170a326b1e0000
database_principal_name:dbo
target_server_principal_name:
target_server_principal_sid:
target_database_principal_name:
server_instance_name:SERVERNAME\OTPMSSQL
database_name:DBA
schema_name:
object_name:DBA
statement:ALTER DATABASE [DBA] MODIFY FILE ( NAME = N'DBA_log', FILEGROWTH = 1048576KB )
additional_information:
.
Collapse
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Seems like those field have been extracted twice by Splunk making it a multivalued field. Check your props.conf for the sourcetype to see if there are two configuration setup for field extraction.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Not sure if your data is coming in JSON or not, but I've seen the same issue with KV extractions with JSON. I had to add a local props.conf with the below stanza to the SH to resolve. This disabled the KV_MODE config on the SH.
[source::foo]
KV_MODE = NONE
You can disable the KV_MODE on either the SH or the forwarder. Disabling on the forwarder will use search-time extractions, disabling on SH will use index-time extractions.
Again, not sure if your data is JSON or not, but hope this helps.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This answer helped me more then the answer marked as solution.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
i couldn't agree more
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Seems like those field have been extracted twice by Splunk making it a multivalued field. Check your props.conf for the sourcetype to see if there are two configuration setup for field extraction.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you! That put me on the right track. I used nomv to eliminate the multivalue.
index=* ComputerName="serverhostname" EventCode=33205 | nomv statement | table ComputerName, statement
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @rob.gibson - Did this search that you posted help to resolve your issue?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, specifically adding "| nomv statement |" corrected the issue.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Another option would be this
index=* ComputerName="serverhostname" EventCode=33205 | table ComputerName, statement | eval statement=mvindex(statement,0)