- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Unable to follow Step 10 of Security Investigati...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Unable to follow Step 10 of Security Investigation Online Experience Endpoint Example
Hi,
I'm doing the exercise at https://www.splunk.com/blog/2017/05/13/steering-clear-of-the-wannacry-or-wanna-decryptor-ransomware-....
Step 10 was to search for the following syntax:
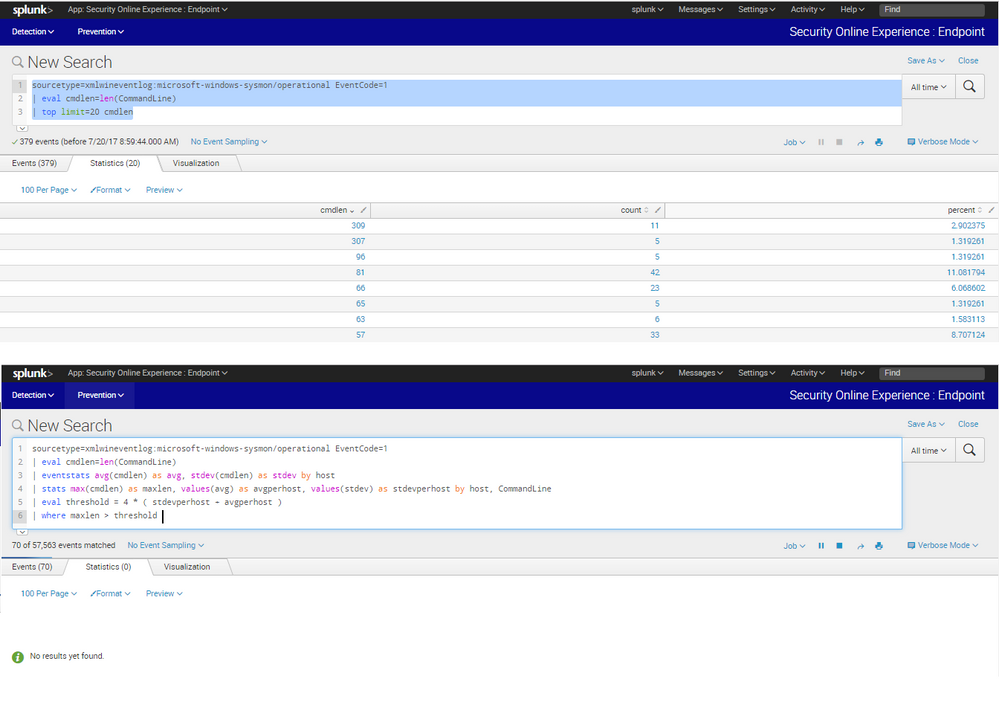
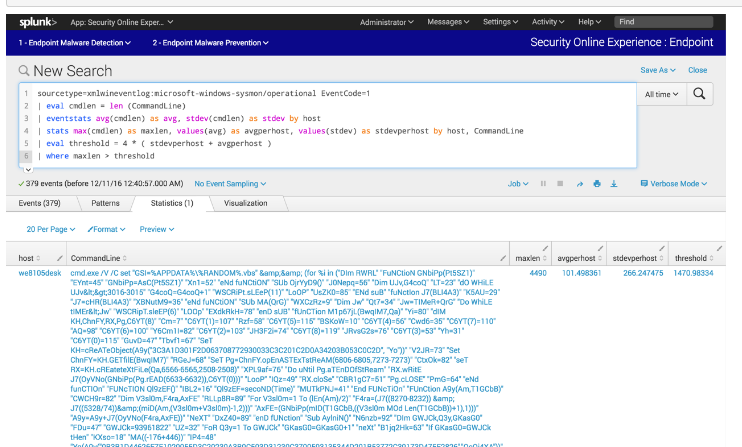
sourcetype=xmlwineventlog:microsoft-windows-sysmon/operational EventCode=1
| eval cmdlen=len(CommandLine)
| eventstats avg(cmdlen) as avg, stdev(cmdlen) as stdev by host
| stats max(cmdlen) as maxlen, values(avg) as avgperhost, values(stdev) as stdevperhost by host, CommandLine
| eval threshold = 4 * ( stdevperhost + avgperhost )
| where maxlen > threshold
Example returned an event with maxlen = 4490 but when I tried it on the "Launch Online Session" with the same search, I cannotfind that event.
I went to analyze the logs again and found that the maxlen is only 309. Step 1 to Step 9 were very accurate. What did I do wrong??
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello again @wuming79. Your issue in the first screenshot above is that the "top" command is finding the "most prolific command line length values in the dataset" and NOT the "largest command line length value in the dataset."
To demonstrate this point, try this:
sourcetype=xmlwineventlog:microsoft-windows-sysmon/operational EventCode=1
| eval cmdlen=len(CommandLine)
| fields cmdlen
| sort -cmdlen
| table cmdlen
| dedup cmdlen
| head 20
Or maybe this link.