- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Timechart with eventtype
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
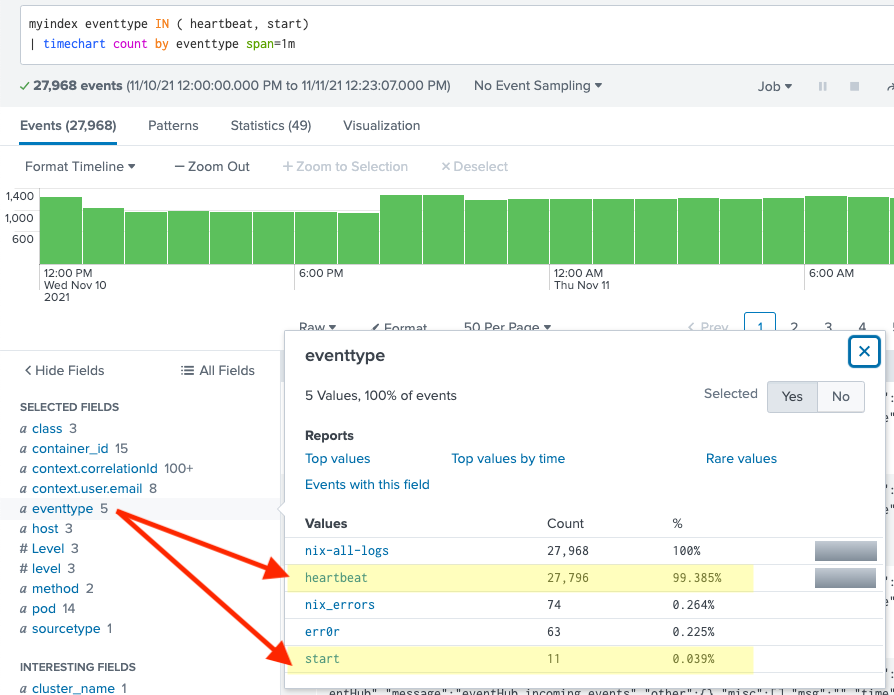
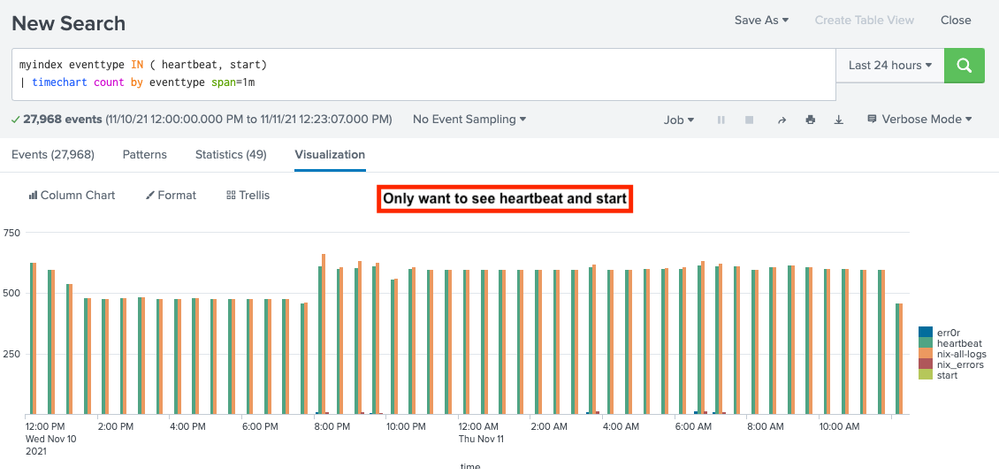
Hello, I am trying to timechart two event types ONLY: heartbeat and start.
However, every event in our Splunk is also mapped as nix-all-logs and few other events by the system admin.
Attached are screenshots. How can I timechart these 2 event types only.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ahhh. Of course. Timechart renders the data as table with eventtypes as columns.
So in order to return only heartbeat eventtype you'd need to not | search but simply
| table _time heartbeat
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
https://docs.splunk.com/Documentation/Splunk/8.2.3/Knowledge/Abouteventtypes
The important part here is that a single event can belong to multiple eventtypes.
So if you want to count only those eventtypes, you have to first search for them, and then filter the results to leave only those two entries.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
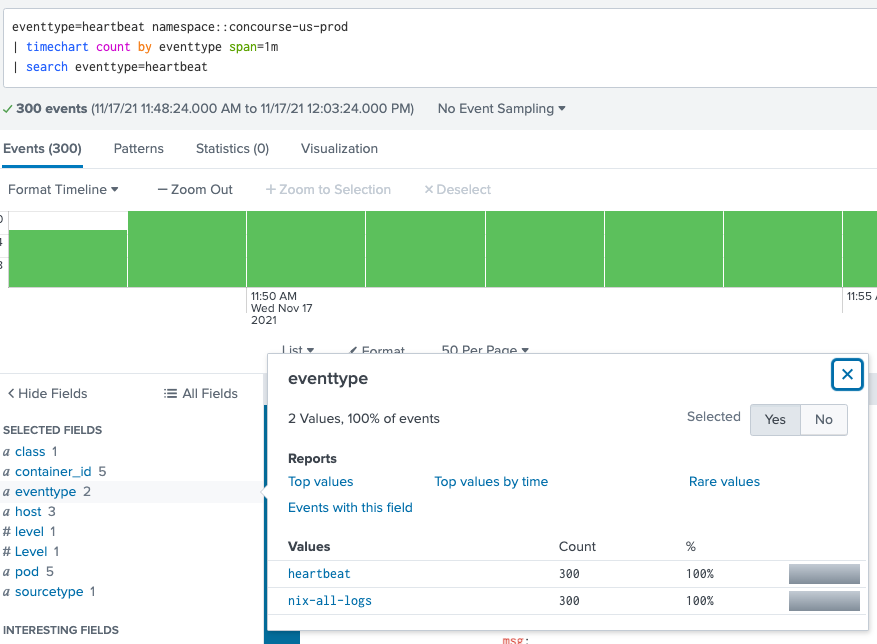
@PickleRick - read through the documentation and tried search first as suggested and then timechart count by eventtype, it did not work. Not sure what i'm doing wrong. any help is appreciated. the eventtype that is present in every events is still present in the chart.
eventtype=heartbeat namespace::my-namespace
| search eventtype=heartbeat
| timechart count by eventtype span=1m
```only want to see eventtype heartbeat```
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Close, but not quite 🙂
Try to understand what you're doing.
Firstly, you search for some events with eventtype=heartbeat. Now everything is ok.
Of those events some will have more than one eventtype.
Then you do
| search eventtype=heartbeat
Which effectively doesn't do anything at this point since all events you find in the previous step had eventtype=heartbeat. So you pass this stepp with your full set of resulting events of which some have more than one eventtype.
Then if you do the timechart by eventtypes of course all your eventtypes will get included in the results
What did you do wrong? You did a search in the wrong place.
You should have done stats first, so you get results for all eventtypes and _then_ search (in the resulting stats) for wanted eventtypes.
eventtype=heartbeat namespace::my-namespace
| timechart count by eventtype span=1
| search eventtype=heartbeat
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
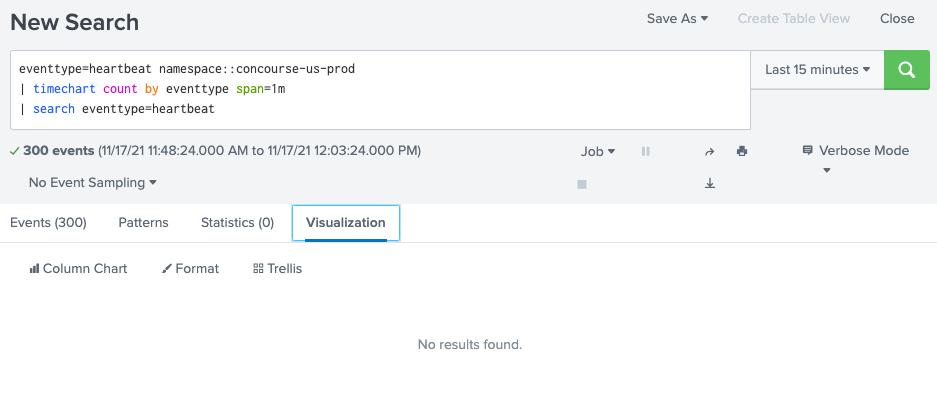
@PickleRick - unfortunately, not able to make it work. The eventtype that is present for every log is still showing up in events tab and timechart tab comes out empty.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ahhh. Of course. Timechart renders the data as table with eventtypes as columns.
So in order to return only heartbeat eventtype you'd need to not | search but simply
| table _time heartbeat