Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Simple search not working but search for NOT != do...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi All,
I hope someone can enlighten me with this seemingly simple problem.
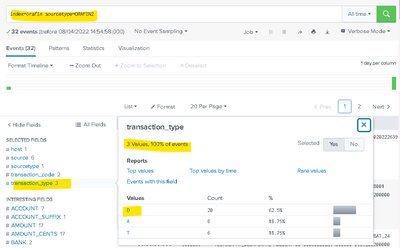
I have this very simple search return 32 rows and showing that all events have a transaction_type value.
If I click on the D highlighted above I would expect it to show me just the 20 D rows but instead I get:
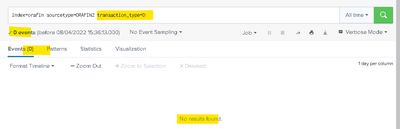
Very weird.
If I change the search to
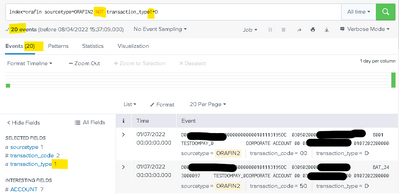
index=orafin sourcetype=ORAFIN2 NOT transaction_type!=D
Then I get what I want:
Can someone please explain what is happening?
Thanks, Keith
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Vatsal,
Thanks for that. Your suggestion works. I would have thought that Splunk would search on the field transaction_type which is extracted at search time as a single character field.
Does this mean if I want to search on the field value (as opposed to words in the _raw) do I need to extract these at index time?
Thanks
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
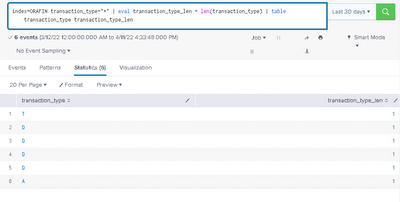
Can you please make sure there is No trailing space in transaction_type fields? Just execute below search and check the transaction_type_len, it should be 1 for value D.
index=orafin sourcetype=ORAFIN2 transaction_type="*"
| eval transaction_type_len = len(transaction_type) | table transaction_type transaction_type_len
Thanks
KV
If any of my reply helps you to solve the problem Or gain knowledge, an upvote would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Kamlesh,
Thanks for the suggestion. I ran what you sent but it shows the field values as 1 byte long.
So its not htat.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@KeithH - Splunk is searching "D" in the _raw log (events). But in the event, it's not D as alone and that is the reason it is not working. If this is the case then use the following instead:
index=orafin sourcetype=ORAFIN2 transaction_type="D*"
I hope this helps!!!!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Vatsal,
Thanks for that. Your suggestion works. I would have thought that Splunk would search on the field transaction_type which is extracted at search time as a single character field.
Does this mean if I want to search on the field value (as opposed to words in the _raw) do I need to extract these at index time?
Thanks
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can use index-time extraction if you want better performance.
Just make sure your search syntax will be something like the below:
index=orafin sourcetype=ORAFIN2 indexed_transaction_type::D
-----
If this was helpful, an upvote would be appreciated!!!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oh - I am running Enterprise version 8.2.4