- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Search for splunk event which has greater than sym...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
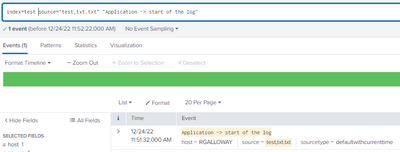
I have a Splunk event "Application -> start of the log".
When I try to search for this log using the exact text then I do not get any results.
I see that the greater than symbol is causing the problem. When I split my search command as "Application -" AND "start of the log" then splunk was able to find the event.
So how do I escape the greater than symbol in splunk search command? I tried > which didn't work.
(I also want to use this search text in "transaction startswith=" command so I cannot use `AND` condition)
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have no problems searching for the '>' character.
Please share your exact SPL and a sample event so we have a better view of the problem. What version of Splunk are you using?
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have no problems searching for the '>' character.
Please share your exact SPL and a sample event so we have a better view of the problem. What version of Splunk are you using?
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, I saw the RAW event and found that the text in the event is "Application -\u003e start of the log"
The greater than symbol is in unicode.
So I have to search as "Application -\\u003e start of the log".
Thank you.