- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How to parse XML and props.conf?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is very similar to a lot of XML parsing questions, however I have read through ~20 topics and am still unable to get my XML log to parse properly.
Here is a sample of my XML file:
<?xml version="1.0" encoding="UTF-8"?><AuditMessage xmlns:xsi="XMLSchema-instance" xsi:noNamespaceSchemaLocation="HL7-audit-message-payload_1_3.xsd"><EventIdentification EventActionCode="R" EventDateTime="2022-11-07T04:18:01"></EventIdentification></AuditMessage>
<?xml version="1.0" encoding="UTF-8"?><AuditMessage xmlns:xsi="XMLSchema-instance" xsi:noNamespaceSchemaLocation="HL7-audit-message-payload_1_3.xsd"><EventIdentification EventActionCode="E" EventDateTime="2022-11-07T05:18:01"></EventIdentification></AuditMessage>
Here are the entire contents of my props.conf file:
[xxx:xxx:audit:xml]
MUST_BREAK_AFTER = \</AuditMessage\>
KV_MODE = xml
LINE_BREAKER = ([\r\n]+)
NO_BINARY_CHECK = true
SHOULD_LINEMERGE = true
TIMESTAMP_FIELDS = <EventDateTime>
TIME_PREFIX = <EventDateTime>
TIME_FORMAT = %Y-%m-%dT%H:%M:%S
category = Custom
disabled = false
I would need your assistance to parse the events.
Thank you.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @poojithavasanth,
I think you didn't use my settings as they are. Please remove TIMESTAMP_FIELDS setting.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Perfect. Thank you!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @poojithavasanth,
I think you didn't use my settings as they are. Please remove TIMESTAMP_FIELDS setting.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you @richgalloway and @scelikok
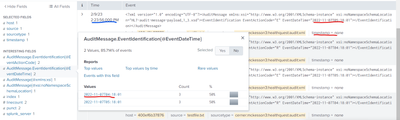
I did not get any error; however, I see timestamp being none.
Also, the timestamp in the file is not same as the timestamp which is marked in blue.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @poojithavasanth,
Below should work;
[xxx:xxx:audit:xml]
SHOULD_LINEMERGE=false
LINE_BREAKER=([\r\n]+)
NO_BINARY_CHECK=true
KV_MODE=xml
TIME_FORMAT=%Y-%m-%dT%H:%M:%S
TIME_PREFIX=EventDateTime="
MAX_TIMESTAMP_LOOKAHEAD=19- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the reply @richgalloway
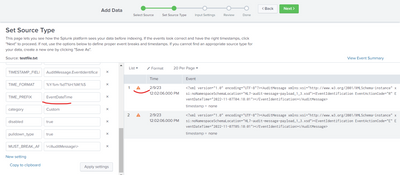
I removed angle brackers for TIME_PREFIX and it did not work.
I would want to extract timestamp and other fields from the event to display them.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Looks like we need to be more explicit with the time prefix. Try this
TIME_PREFIX = EventDateTime="If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What exactly are you getting for results? What does "parse properly" mean to you?
I can see that the TIME_PREFIX setting is incorrect. Remove the angle brackets and it should work.
Also, the TIMESTAMP_FIELDS setting only applies when INDEXED_EXTRACTIONS is used.
If this reply helps you, Karma would be appreciated.