Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Splunk Search
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Optimize my search
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
jyab6z
Path Finder
03-21-2019
06:40 AM
This is my search:
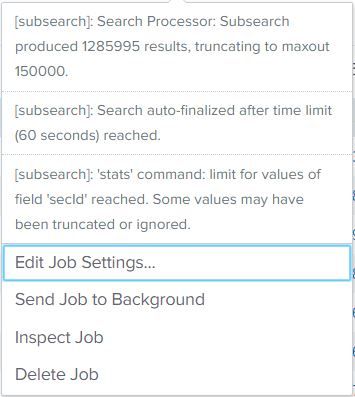
Function="- Parts::GetPartSection =>" | rex "maingroupNo\>(?.+)\\(?.+)\\(?.+)\" | convert timeformat="%H:%M:%S" dur2sec(TimeInSec) | stats count first(TimeInSec) AS endTime last(TimeInSec) AS startTime by UserID DATE maingroup subgroup | appendcols [search Function="- Parts::GetPartSection =>" | rex "maingroupNo\>(?.+)\\(?.+)\\(?.+)\" | stats list(secId) as secId_new by UserID DATE maingroup subgroup] | where count > 5 | eval Time_diff = abs(endTime - startTime) | eval avgTime_count = Time_diff/count | where avgTime_count < 20 | where maingroup=="03" AND subgroup=="26" | mvexpand secId_new | stats count by secId_new | rename secId_new as Avsnitt
THEN got this error when it runs over 1 year's data.
Any ideas?
Thanks in advance!
1 Solution
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
richgalloway

SplunkTrust
03-21-2019
08:44 AM
The subsearch is trying to process too much data. Why do you even need it? You should be able to combine the two searches into a single search. See if this accomplishes the same task.
Function="- Parts::GetPartSection =>" | rex "maingroupNo\>(?.+)\\(?.+)\\(?.+)\" | convert timeformat="%H:%M:%S" dur2sec(TimeInSec) | stats count first(TimeInSec) AS endTime, last(TimeInSec) AS startTime, list(secId) as secId_new by UserID DATE maingroup subgroup | where count > 5 | eval Time_diff = abs(endTime - startTime) | eval avgTime_count = Time_diff/count | where avgTime_count < 20 | where maingroup=="03" AND subgroup=="26" | mvexpand secId_new | stats count by secId_new | rename secId_new as Avsnitt
---
If this reply helps you, Karma would be appreciated.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
richgalloway

SplunkTrust
03-21-2019
08:44 AM
The subsearch is trying to process too much data. Why do you even need it? You should be able to combine the two searches into a single search. See if this accomplishes the same task.
Function="- Parts::GetPartSection =>" | rex "maingroupNo\>(?.+)\\(?.+)\\(?.+)\" | convert timeformat="%H:%M:%S" dur2sec(TimeInSec) | stats count first(TimeInSec) AS endTime, last(TimeInSec) AS startTime, list(secId) as secId_new by UserID DATE maingroup subgroup | where count > 5 | eval Time_diff = abs(endTime - startTime) | eval avgTime_count = Time_diff/count | where avgTime_count < 20 | where maingroup=="03" AND subgroup=="26" | mvexpand secId_new | stats count by secId_new | rename secId_new as Avsnitt
---
If this reply helps you, Karma would be appreciated.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
jyab6z
Path Finder
03-22-2019
12:11 AM
Ohh, thank you!
It helps!!!
Get Updates on the Splunk Community!
Webinar Recap | Revolutionizing IT Operations: The Transformative Power of AI and ML ...
The Transformative Power of AI and ML in Enhancing Observability
In the realm of IT operations, the ...
.conf24 | Registration Open!
Hello, hello! I come bearing good news: Registration for .conf24 is now open!
conf is Splunk’s rad annual ...
ICYMI - Check out the latest releases of Splunk Edge Processor
Splunk is pleased to announce the latest enhancements to Splunk Edge Processor.
HEC Receiver authorization ...