- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: Need Help with a search where I am using strea...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Need help with a search where I am using streamstats and timechart?
I am trying to create a search where if there is a change of 30 percent within 5 mins of a few field values, I would like to create an alert.
The search should take a sum of the field values where field names are like traffic_in#abc and traffic_out#abc, and then use delta command to find difference between current and previous values. Now, the issue is I have 11 field values like abc(e.g., abc, cde,efg etc.) and I want delta of total of (traffic_in#***+traffic_out#***) and then find the values when traffic has changed by over 30%.
The search that I have can be used when I have only one value like abc, but I want to change it so that it can work with multiple values.
The search is :
eventtype=cacti:mirage host="onl-cacti-02" host_id=193 ldi IN("8835","8836","8837","8839","8840","8841","8846","8847","8848","8843","8844",)
| reverse
| eval combination=rrdn+"#"+name_cache
| streamstats current=t window=2 global=f range(_time) as deltaTime range(rrdv) AS rrd_value_delta by combination
| eval isTraffic = if(like(rrdn,"%traffic%"),1,0)
| eval kpi = if(isTraffic==1,rrd_value_delta*8/deltaTime,rrd_value_delta/deltaTime)
| timechart limit=0 useother=f span=5min last(kpi) by combination
| addtotals fieldname=total
| delta total as change
| eval change_percent=change/(total-change)*100
| timechart span=5min first(total) AS total_traffic, first(change_percent) AS traffic_change
| where abs(traffic_change) > 30
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Are you trying to measure for a 30% difference for any one of the values?
In other words: "If any of these values (combination) have a difference of >30%, then fire an alert"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, that's what I want. When a sum of field value of any(traffic_in#xyz and traffic_out#xyz) at let's say 12:15 is greater than 30% of the same at 12:10, fire an alert and show all of those fields where this condition is satisfied.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I think part of your problem is that you are losing the reference to the "combination" field by doing your first timechart.
You could try something like the following:
(Note: I have not tested this as I do not have access to your data)
eventtype=cacti:mirage host="onl-cacti-02" host_id=193 ldi IN("8835","8836","8837","8839","8840","8841","8846","8847","8848","8843","8844",)
| reverse
| eval combination=rrdn+"#"+name_cache
| streamstats current=t window=2 global=f range(_time) as deltaTime range(rrdv) AS rrd_value_delta by combination
| eval isTraffic = if(like(rrdn,"%traffic%"),1,0)
| eval kpi = if(isTraffic==1,rrd_value_delta*8/deltaTime,rrd_value_delta/deltaTime)
| bucket _time span=5m
| stats last(kpi) as last_kpi by combination _time
| sort combination _time
| streamstats current=t window=2 range(last_kpi) as last_kpi_diff by combination
| eval change_percent=(last_kpi/(last_kpi-last_kpi_diff))*100
| where change_percent>30 AND last_kpi_diff!=0
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It still didn't actually solve my problem. I need some formula that can accurately determine the percentage.
E.g., if I have values like 2,10 and and so on and last_kpi_diff is 8, then change is abs(10/(10-8)*100)=500, that's ok.
But, if I have values like 10,2 and so on and last_kpi_diff is 8, then change is abs(2/(2-8)*100)=33, which is not ok. Change should have been 20 here with abs(2/(2-(-8)))=20.
Need some functionality that can give the actual difference rather than absolute difference as given by range() function. I know there isn't any function that gives actual difference.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It might also be possible for you to get rid of the first streamstats and just construct the table you need using stats, and then doing the second streamstats (as you can see in my suggestion above) to get the difference in the values.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
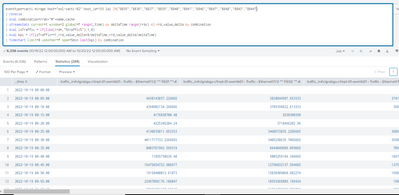
The search output with a part of the search is