- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Need help editing my search string so it displays ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Below is my search string:
| multisearch [search index="*" host="*" sourcetype="*" user="*" useradd "type=ADD_GROUP" | eval rectype1="Created new user"] [search index=* host=* sourcetype="*" "usermod" AND "type=USER_MGMT" | eval rectype2="Added new user to group"] [search host="*" index="*" sourcetype="*" "su:" "session opened for user" | eval Date=strftime(_time, "%Y/%m/%d") | rex "by (?[^(]+)" | rex "^[^\)\n]*\):\s+\w+\s+\w+\s+\w+\s+\w+\s+(?P\w+)" | eval rectype3= "Switched to different user account"] [search index=* host=* sourcetype="*" user="*" "type=USER_CMD"(action=success OR action=failure OR action=unknown) | eval rectype4="Executed sudo command"] | stats dc(rectype4) as "Executed sudo command", dc(rectype3) as "Switched to different user account" , dc(rectype2) as "Added new user to group", dc(rectype1) as "Created new user" by user
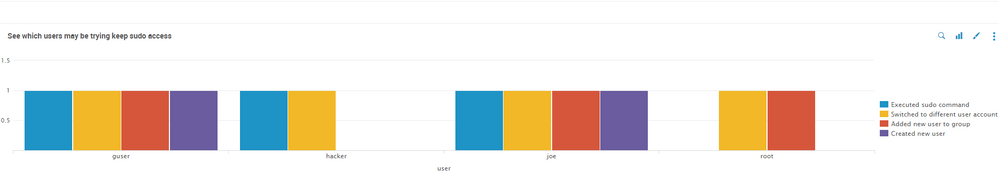
Below is my image of the results:
You can see that these users have committed these actions listed on the right side of the chart such as, executing sudo commands, creating new users etc etc and that why they are listed on the chart, however, each bar for each user is the same height as the others. I want the bars to be measured buy the count of how many times a user has commit these actions. For example, if user hacker switches to a different user account 5 different times, that yellow block will be at a height of 5 according to a numbered range on the left side of the chart. Right now the numbered range on the left side is 0.5 to 1.5 and I don't understand why that is.
how can I accomplish this?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@jcorkey, change from distinct count i.e. dc() to count i.e. count()
| stats count(rectype4) as "Executed sudo command", count(rectype3) as "Switched to different user account" , count(rectype2) as "Added new user to group", count(rectype1) as "Created new user" by user
| makeresults | eval message= "Happy Splunking!!!"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@jcorkey, change from distinct count i.e. dc() to count i.e. count()
| stats count(rectype4) as "Executed sudo command", count(rectype3) as "Switched to different user account" , count(rectype2) as "Added new user to group", count(rectype1) as "Created new user" by user
| makeresults | eval message= "Happy Splunking!!!"