- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Missing original value after using distinct query
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Missing original value after using distinct query
Hi,
I am having the following issue that need your help.
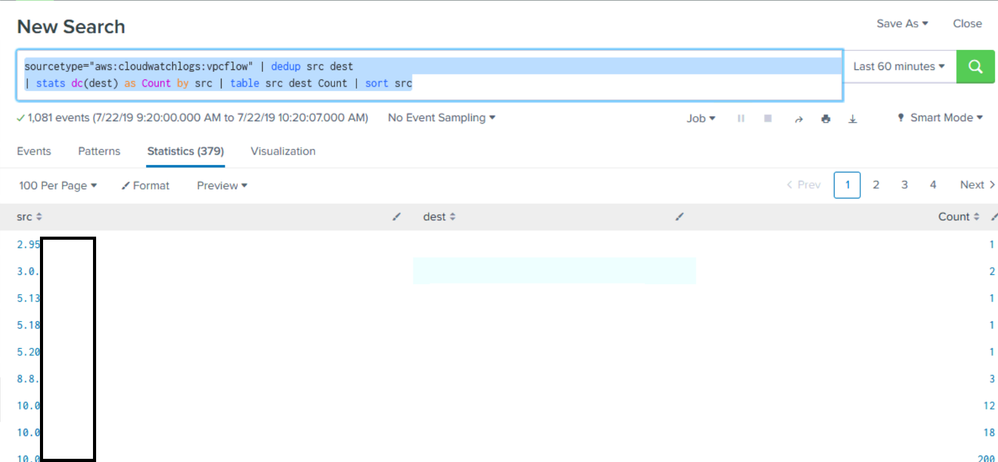
The scenario is: I am working on the report of firewall data in Splunk. The requirement is getting the distinct destination connected by source address. The table should contain: Source Address, Destination Address and Distinct count the number of Destination address connected by Source.
I am trying to use the dc query to get the distinct count for destination address but when doing table, i only can get source and distinct count number but the destination address value is missing.
Here is the query that I am using:
sourcetype="aws:cloudwatchlogs:vpcflow"
| dedup src dest | stats dc(dest) as
Count by src | table src dest Count |
sort src
Below is the output of the query:
Please help to suggest what query should I use to retain the destination address value.
Thanks,
Michael
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@michaelhoang ,
Try
sourcetype="aws:cloudwatchlogs:vpcflow"
| stats dc(dest) as Count,values(dest) as dest by src
OR
sourcetype="aws:cloudwatchlogs:vpcflow"
| stats dc(dest) as Count by src,dest|eventstats sum(Count) as Count by src