Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Splunk Search
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Merge multiple rows into one of a field
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Merge multiple rows into one of a field
obularajud16
Explorer
08-31-2020
06:37 AM
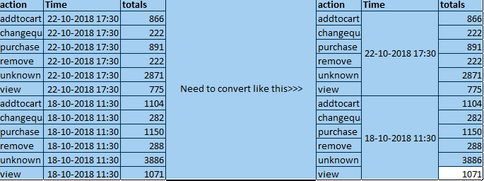
With the below query I am able to get data as below(first one) and I need to convert it as second box
For the time field I am getting common values and i need to merge and combine them as shown. is there any way to achieve this, I've tried with values() but it is not working
sourcetype=access_combined | eval action = if(isnull(action) OR action="", "unknown", action) | bin _time span=102h |eval Time=strftime(_time,"%Y-%m-%d %H:%M:%S") | stats count as totals by action,Time | sort -Time,action
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
ITWhisperer

SplunkTrust
08-31-2020
06:51 AM
Have you tried adding
...
| stats values(action) as action, values(totals) as totals by Time
| fields action, Time, totals
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
obularajud16
Explorer
08-31-2020
11:29 AM
Yes, but it's not worked.
Get Updates on the Splunk Community!
Announcing Scheduled Export GA for Dashboard Studio
We're excited to announce the general availability of Scheduled Export for Dashboard Studio. Starting in ...
Extending Observability Content to Splunk Cloud
Watch Now!
In this Extending Observability Content to Splunk Cloud Tech Talk, you'll see how to leverage ...
More Control Over Your Monitoring Costs with Archived Metrics GA in US-AWS!
What if there was a way you could keep all the metrics data you need while saving on storage costs?This is now ...