- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: Matching Results of a Search on One Value - Ba...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
I am trying to configure alerting for a Failover Cluster by verifying the running server name, then confirming that the windows services on said server is running as expected. We have two servers in the cluster that could change anytime, where the one that is active should always have the windows services running (and alert if they are not and it is the active host) and the passive server should have the services stopped (expected, no alert).
The two WMI events that I have running on the two hosts are below:
This event shows the active failover server:
Server=Server1
ComputerName=Cluster
wmi_type=PIAnalysisCluster
The below events shows the Windows Service events on either host:
Caption=Cluster Service
DisplayName=Cluster Service
Name=ClusSvc
ProcessId=3192
StartName=LocalSystem
State=Running
Status=OK
SystemName=Server1
wmi_type=ClusterService
20210325160700.359614
Caption=Cluster Service
DisplayName=Cluster Service
Name=ClusSvc
ProcessId=3040
StartName=LocalSystem
State=Running
Status=OK
SystemName=Server2
wmi_type=ClusterService
What i am trying to do is just show where Server=Server1 is active, then show just the status of the Windows Server from SystemName=Server1. I've tried with "eval Server=coalesce(SystemName,Server)", evals on match (Server==SystemName) as well "where Server=SystemName", but I have been unable to find a way to just show the active server based on the first event, and match the server name based on the second event with the status of the Windows Service.
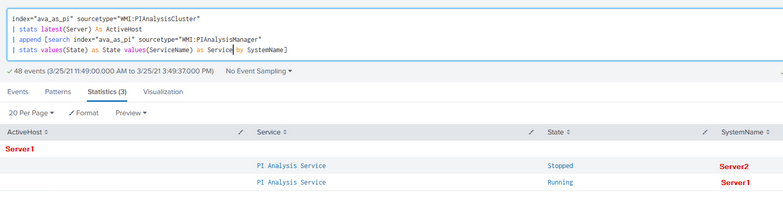
Example attached of what the data looks like without attempting to join the values.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Add this to the end of the query
| filldown ActiveHost
| where ActiveHost=SystemName- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Add this to the end of the query
| filldown ActiveHost
| where ActiveHost=SystemName- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This worked perfectly! Thank you very much, bowesmana!