Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: Is it possible to use base search in append su...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I want to use base search for query2 as well
Thanks!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Here's a run-anywhere example (concept courtesy of @sowings):
<dashboard>
<label>616340</label>
<search id="subsearch_results">
<query>index=_internal | stats count BY sourcetype | table sourcetype</query>
<earliest>-24h@h</earliest>
<latest>now</latest>
<done>
<condition>
<set token="subsearch_sid">$job.sid$</set>
</condition>
</done>
</search>
<row>
<panel>
<event>
<search>
<query>index=_internal [| loadjob $subsearch_sid$]</query>
<earliest>-24h@h</earliest>
<latest>now</latest>
<sampleRatio>1</sampleRatio>
</search>
<option name="list.drilldown">none</option>
</event>
</panel>
</row>
</dashboard>
The key is having your base search set a token with its sid and fetching its results in the subsearch via loadjob.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Here's a run-anywhere example (concept courtesy of @sowings):
<dashboard>
<label>616340</label>
<search id="subsearch_results">
<query>index=_internal | stats count BY sourcetype | table sourcetype</query>
<earliest>-24h@h</earliest>
<latest>now</latest>
<done>
<condition>
<set token="subsearch_sid">$job.sid$</set>
</condition>
</done>
</search>
<row>
<panel>
<event>
<search>
<query>index=_internal [| loadjob $subsearch_sid$]</query>
<earliest>-24h@h</earliest>
<latest>now</latest>
<sampleRatio>1</sampleRatio>
</search>
<option name="list.drilldown">none</option>
</event>
</panel>
</row>
</dashboard>
The key is having your base search set a token with its sid and fetching its results in the subsearch via loadjob.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Pasting this answer into a new dashboard (Splunk Enterprise 8.02) produces:
- " Search is waiting for input..." for about a minute
- a list of events rather than a table intended as a result
Has something changed in Splunk 8 that this no longer works?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can use this to have in effect multiple separate base searches that feed into one, and you can also use this to conditionally only run base searches that haven't already been ran
https://answers.splunk.com/answers/738095/dashboard-search-optimization-only-run-searches-wh.html
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Wow, but im facing no results found in post processing searches as my base search runs longer, any idea how to resolve this?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Wow!! This is such a COOL trick!! This is the kind of stuff that dreams are made of! Thank you for sharing!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you so much!!!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can try chained post-process searches
have a look at this doc
http://docs.splunk.com/Documentation/Splunk/latest/Viz/Savedsearches#Examples_2
<search id="baseSearch">
<query>index=_internal</query>
<earliest>-60m@m</earliest>
<latest>now</latest>
</search>
<search base="baseSearch" id="post_process_1">
<query>sourcetype=splunkd</query>
</search>
<search base="post_process_1" id="post_process_2">
<query>stats count</query>
</search>
let me know if this helps!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
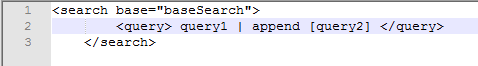
Thanks for your response however I need to use base search inside append sub search
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is not very usefull. Once you run the search base and calls it later, the search comes with " | " .
In the example, index=xxx sourcetype=zzzz must be together, if you split them as "index=xxx | sourcetype=zzz" it will break the search.
I'm facing this problema right now and still doesn't figured out how to fix it.
I have few querys such as:
1 search - a a b b c c d d e e
2 search - a a b b c c d d
3 search - a a c c d d
4 search - a a d d e e
a = index
b = sourcetype
c = user
d = host
i tried:
<query>index=_internal</query>
<earliest>-60m@m</earliest>
<latest>now</latest>
<query>sourcetype=splunkd</query>
But got the result:
index=_internal | sourcetype=splunkd
and the error: unknow command sourcetype
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can define your query in a token that can be set in an init section of your dashboard. Here's an example:
<form>
...
<init>
<set token="query">your repetitve search</set>
</init>
<row>
<panel>
<event>
<title>Tokenized Based Query</title>
<search id="baseSearch">
<query>$query$</query>
<earliest>-24h@h</earliest>
<latest>now</latest>
</search>
<option name="list.drilldown">none</option>
</event>
<event>
<title>Tokenized Append Search</title>
<search base="baseSearch">
<query>| $query$</query>
</search>
<option name="list.drilldown">none</option>
</event>
</panel>
</row>
</form>
Note that you don't need to state the base search in your postprocess seach.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the quick reply!
I have few doubts regarding how base search works.When we use base search does it run every time we use it in post process search or it run once and the data is then used in every search?
Here also does the query in the token value is executed once or every time?
Actually my base search is dbxquery and I don't want to hit the database again and again.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The base search will only run once and the post-process search will use the cached base search as starting point for its post-process search. However if your base search needs to be refreshed it will influence all post-process searches that are based on it.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I forgot to mention I can't set the query in init section as it is using token values from from input and those changes will not be reflected in the query if it is defined in init section:(
So there is no direct way to use base search in append?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Okay then how about setting the token in the done section of the search? Although I could not find a solution to get the real search string, try this with the optimizedSearch string as shown:
<panel>
<event>
<title>Base Search</title>
<search id="baseSearch">
<query>index=_internal | where $earliest$ > 0</query>
<earliest>-24h@h</earliest>
<latest>now</latest>
<done>
<set token="query">$job.optimizedSearch$</set>
</done>
</search>
<option name="list.drilldown">none</option>
</event>
</panel>
<panel>
<event>
<title>Double used Base Search</title>
<search base="baseSearch">
<query>$query$</query>
</search>
<option name="list.drilldown">none</option>
</event>
</panel>
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sadly this isn't working in my dashboard.
I have one concern though. Even if we somehow manage to pass the query as a token wouldn't it be equivalent to writing the query itself. I don't think it is not going to improve the performance. I wanted to use the base search in append so that I don't have to run the query twice and the performance of my dashboard can be improved.Please correct me if I am wrong.