- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Is it possible to create Time chart with search wi...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is it possible to create Time chart with search with base search?
I have a dashboard with the following base search:
<search id="CreatedDossierCount">
<query>index="customer1-closecl-prod-long" application="closecl" transactionType="createDossier"</query>
<earliest>$field1.earliest$</earliest>
<latest>$field1.latest$</latest>
</search>
and several panels based on this search, this simple one is working fine:
<panel>
<title>Aantal aanvragen vandaag</title>
<single>
<title>Aantal aanvragen</title>
<search base="CreatedDossierCount">
<query> stats count</query>
</search>
<option name="drilldown">none</option>
<option name="trellis.enabled">0</option>
<option name="trellis.size">medium</option>
</single>
</panel>
gives me a number 35 at the moment.
but a second one with a time chart is not:
<panel>
<title>Aantal aanvragen per tijdseenheid</title>
<table>
<search base="CreatedDossierCount">
<query>timechart minspan=1d bins=12 dc(dossierId) as count | fillnull</query>
</search>
<option name="drilldown">none</option>
<option name="link.inspectSearch.visible">1</option>
<option name="link.openSearch.visible">1</option>
</table>
</panel>
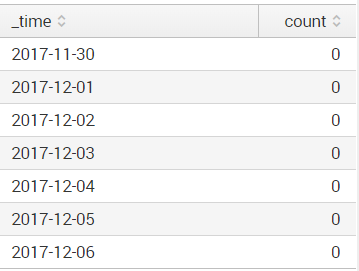
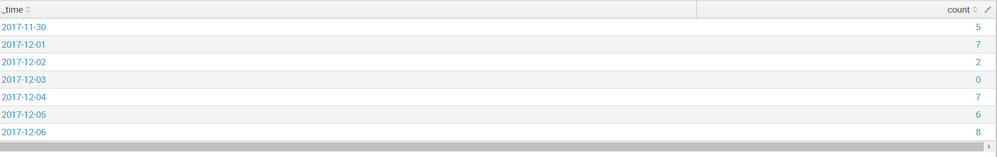
it gives me this result:
if I then open in search I get this search from it:
index="customer1-closecl-prod-long" application="closecl" transactionType="createDossier" | timechart minspan=1d bins=12 dc(dossierId) as count | fillnull
as expected. Which gives me this result:
I even tried creating a dashboard panel from that search again, which gives me the same proper result, but if I move the first part of the search to the basesearch again I get the zeroes back.
This leads me to believe it is the combination of the base search and timechart. But I could be wrong.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I think you have missed out a pipe on the the query?
timechart
Should be:
| timechart
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I suspect you are running into this issue:
In post-process searches, reference fields that are also referenced in the base search. If you are not referencing a particular field in the base search, do not reference it in the post-process search. Fields without a reference in the base search appear null in a post-process search. The post-process search returns no results in this case.
Source: http://docs.splunk.com/Documentation/Splunk/latest/Viz/Savedsearches
So you could try adding | fields * to the base search in order to ensure the field is preserved. But the same documentation also mentions other pitfalls of using post-processing on a search that involves no transforming commands. Given that your base search does not use any transforming commands, I think you may not get any benefit from using that as a base search anyway, and you may be best served by just using the whole query in the place where you've been trying to use a post-processed search.