- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: How to use regex to filter out Windows events ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to use regex to filter out Windows events with Account names ending with $?
Hi
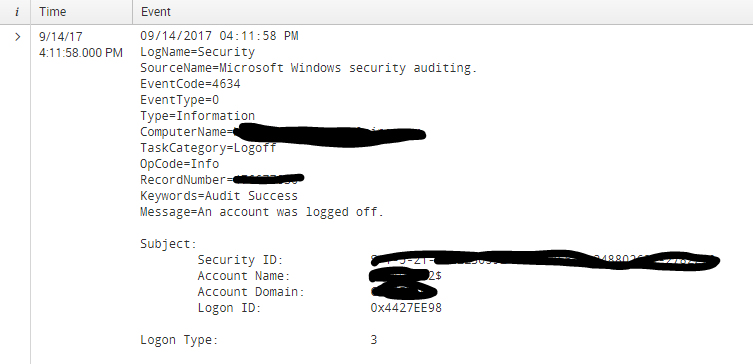
How to edit props.conf and transforms.conf to exclude the windows events with event Codes 4634 at indexing time and Account_Name ending with $? Below is the sample event
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Why don't you try blacklist in inputs.conf if you are on universal forwarder?
[your stanza / what you are monitoring]
blacklist = 400
will ignore all 400 type errors
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I recommend not using a regular expression.
<base search> NOT (EventCode="4634" OR Account_Name="*$")
If you're set on using regular expressions, try the following.
<base search>
| regex Account_Name!="\$$"
| regex EventCode!="4634"
Both searches assume you've extracted those fields. You can create a regular expression to search against the raw field, but I recommend searching against extracted fields.
If you want to go a step further, try mapping it to the Splunk CIM, and then searching against the CIM field names.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I want to ignore them at indexing time
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@kiran331 Did you find the correct regex to blacklist Account name ending with $ at index time
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I recommend changing your question title and summary to include the information from your comment, or you might get answers that don't address your situation.