- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: How to use part of field names for grouping op...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have log messages in the following format:
_time=... a_foo=10 a_bar=1 a_baz=20
_time=... a_foo=1 a_bar=2 a_baz=1
_time=... a_foo=5 a_bar=5 a_baz=3
I want to take all fields starting with 'a_' and use the second part of the field name as the value which is used for a grouping operation
That means, when I'm using a query like this:
index=foo | ...<insert magic here>... | stats sum(...) by ...
a result like this should be returned:
foo=16 bar=8 baz=24
Is a transformation like this somehow possible?
Thank you!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi zaphod1984,
sure you can do this in Splunk 😉 Using stats you can run this run everywhere search to learn how this can be done:
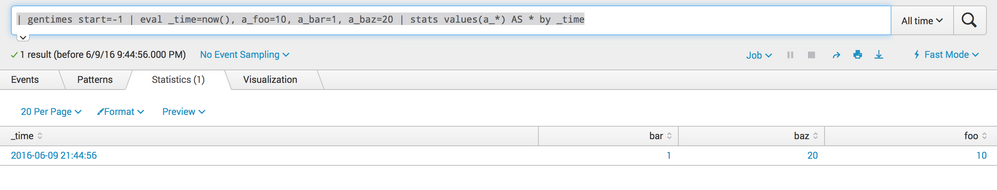
| gentimes start=-1 | eval _time=now(), a_foo=10, a_bar=1, a_baz=20 | stats values(a_*) AS * by _time
the result looks like this:
Hope this helps and if not, adapt it to your needs ...
cheers, MuS
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I found out how to do it by myself, for future reference:
first i filter all the fields that are interesting to me (the a_* fields), than via sum(*) as * a sum is built over every field in the result set with the name of the field as the column, hence the as * part.
index=foo | fields + a_* | stats sum(*) as *
this leaves us with a result in the form
a_foo a_bar a_baz
16 8 24
if we now want to do a pie chart over the result strange things happen as the pie chart only takes the values of the first columns into acount, this can be easily mitigated via transpose:
index=foo | fields + a_* | stats sum(*) as * | transpose
the result now is:
a_foo 16
a_bar 8
a_baz 24
for my use case this is perfectly fine, one could additionally to a rename if necessary
if instead of a stat a timechartis required, the following approach works:
like in the stat version filter the fields by a_*, via the table format the order of the columns is changed as for a timechart the _time field has to be the first column. the subsequent timechart command than groups via sum(*) as * like in the stats example
index=foo | fields + a_* | table _time * | timechart span=10m sum(*) as *
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi zaphod1984,
sure you can do this in Splunk 😉 Using stats you can run this run everywhere search to learn how this can be done:
| gentimes start=-1 | eval _time=now(), a_foo=10, a_bar=1, a_baz=20 | stats values(a_*) AS * by _time
the result looks like this:
Hope this helps and if not, adapt it to your needs ...
cheers, MuS
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
thank you very much, you have been a little bit faster than me with answering 🙂
that feature with the implicit extraction from the field name via values(a_*) AS * is very cool!
would this still work if there very multiple combinations like a_foo, a_bar, b_baz?