Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Splunk Search
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
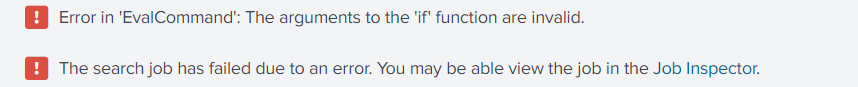
- How to solve this issue with eval if?
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
SumanPalisetty
Path Finder
11-11-2022
08:54 AM
1 Solution
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
richgalloway

SplunkTrust
11-11-2022
09:08 AM
There are too many arguments to the first if. Each if function can have only 3 arguments - an expression to test, the value to set if true, and the value to set if false. If you want nested ifs then it needs to look more like this:
| eval new_field = if(error=200,"sc", if(error=500,"css","ssc"))
---
If this reply helps you, Karma would be appreciated.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
richgalloway

SplunkTrust
11-11-2022
09:08 AM
There are too many arguments to the first if. Each if function can have only 3 arguments - an expression to test, the value to set if true, and the value to set if false. If you want nested ifs then it needs to look more like this:
| eval new_field = if(error=200,"sc", if(error=500,"css","ssc"))
---
If this reply helps you, Karma would be appreciated.
If this reply helps you, Karma would be appreciated.
Get Updates on the Splunk Community!
Updated Team Landing Page in Splunk Observability
We’re making some changes to the team landing page in Splunk Observability, based on your feedback. The ...
New! Splunk Observability Search Enhancements for Splunk APM Services/Traces and ...
Regardless of where you are in Splunk Observability, you can search for relevant APM targets including service ...
Webinar Recap | Revolutionizing IT Operations: The Transformative Power of AI and ML ...
The Transformative Power of AI and ML in Enhancing Observability
In the realm of IT operations, the ...