- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How to separate field
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, guys. I have a big trouble here.
I'm using rex to get ip-adresses.
|rex max_match=0 "(?P<ip0>((?:[0-9]{1,3}\.){3}[0-9]{1,3}.[0-9]{1,9}))"
| field1: |
| 255.255.255.255/1 |
| 255.255.255.255/2 |
| 255.255.255.255/3 |
| 255.255.255.255/4 |
How can i do this? Please, help 😞
I want to get something like this
| field1: | field2: | field3: | field4: |
| 255.255.255.255/1 | 255.255.255.255/2 | 255.255.255.255/3 | 255.255.255.255/4 |
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Dalador,
If every log contains four ip address you can try below;
| rex "(?P<ip1>(?:[0-9]{1,3}\.){3}[0-9]{1,3}.[0-9]{1,9}).+(?P<ip2>(?:[0-9]{1,3}\.){3}[0-9]{1,3}.[0-9]{1,9}).+(?P<ip3>(?:[0-9]{1,3}\.){3}[0-9]{1,3}.[0-9]{1,9}).+(?P<ip4>(?:[0-9]{1,3}\.){3}[0-9]{1,3}.[0-9]{1,9})"- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Dalador,
If every log contains four ip address you can try below;
| rex "(?P<ip1>(?:[0-9]{1,3}\.){3}[0-9]{1,3}.[0-9]{1,9}).+(?P<ip2>(?:[0-9]{1,3}\.){3}[0-9]{1,3}.[0-9]{1,9}).+(?P<ip3>(?:[0-9]{1,3}\.){3}[0-9]{1,3}.[0-9]{1,9}).+(?P<ip4>(?:[0-9]{1,3}\.){3}[0-9]{1,3}.[0-9]{1,9})"- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
yes, exactly what i need!
Thanks, didn't know that we can use rex like this..
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Dalador ,
Try to add :
| transposeThis would create columns based on your rows.
You will probably have to do some renaming and maybe filter some of the new rows, but it should give you what you are asking for.
Best Regards
Ralph
Karma and/or Solution tagging appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, Ralph
Close enough, but i want to get something like this
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This would give you numbered ip* columns
| transpose
| rename "row *" as ip*
| fields - column
This is a modified version of what @ITWhisperer suggested, which is more flexible than my simple transpose approach:
| rename ip0 as ip
| streamstats count as row
| eval row="ip".row
| eval {row}=ip
| stats values(ip*) as ip*
But answering these questions would really help to find a suitable solution 🙂
Karma and/or Solution tagging appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
| makeresults | eval _raw="field1
255.255.255.255/1
255.255.255.255/2
255.255.255.255/3
255.255.255.255/4"
| multikv forceheader=1
| fields field1
| fields - _time _raw
| streamstats count as row
| eval row="field_".row
| eval {row}=field1
| stats values(field_*) as field*- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks,
Unfortunately this is not working for me 😞
I want something like this:
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You are probably going to have to give a bit more detail - is ip0 a multi-value field or are these separate events? are there other fields you want to keep? what is it about the suggestions that is not working for you?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
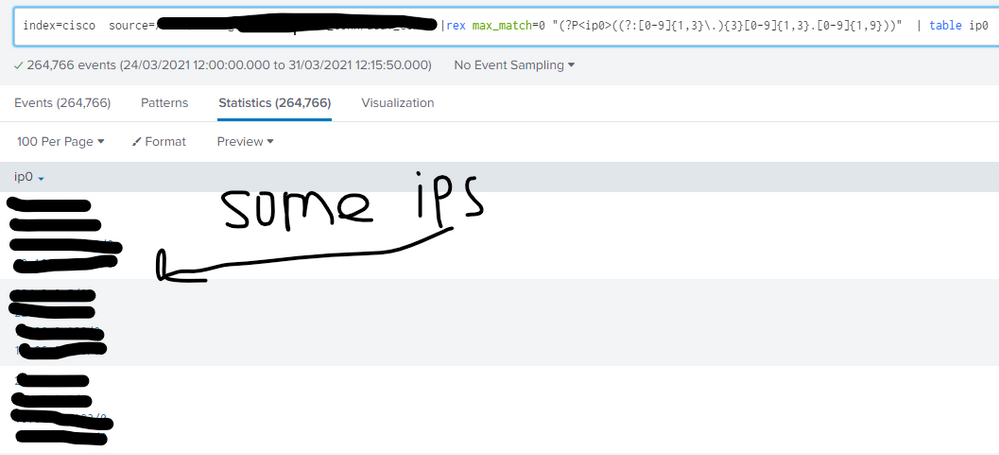
ip0 is a multi-value field, Sorry, i'm new to splunk and i try to do my best
i tried to add your solution to my search string and get empty results 😞
I want just this 4 ip adresses in separate columns, and add _time, i think
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No worries - we all had to start somewhere!
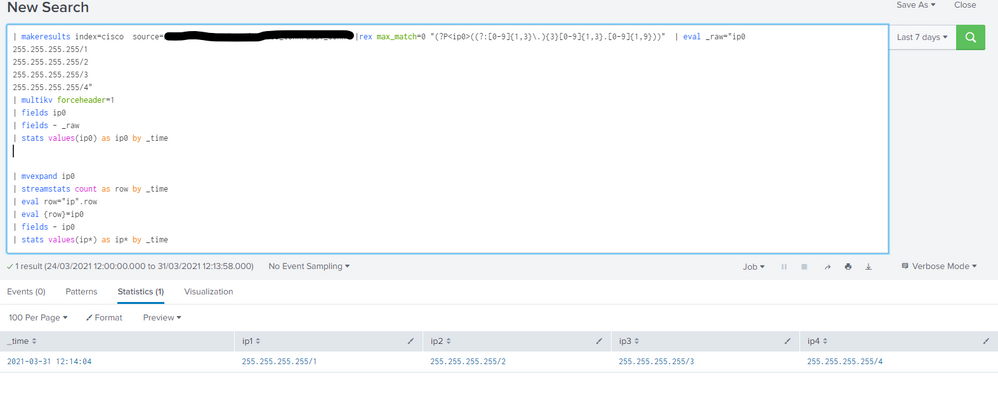
| makeresults | eval _raw="ip0
255.255.255.255/1
255.255.255.255/2
255.255.255.255/3
255.255.255.255/4"
| multikv forceheader=1
| fields ip0
| fields - _raw
| stats values(ip0) as ip0 by _time
| mvexpand ip0
| streamstats count as row by _time
| eval row="ip".row
| eval {row}=ip0
| fields - ip0
| stats values(ip*) as ip* by _timeThe part before the blank lines just set up the dummy data as a multi-value field
The mvexpand converts the multi-value field into separate events
Streamstats identifies the instance of the multi-value field the event came from
eval converts the count to a name for the resultant field
eval with {} uses the contents of the field (row) as the name of the resultant field
fields removes the original field
stats gathers the fields back into a row based on the original time of the event
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yep, this almost looks like i want!
Thanks!
But, how to unite this two search? I tried to |eval _raw="ip0" and get no results
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You don't need the makeresults part before the blank lines - these just set up some dummy data the demonstrate the bit after the blank lines
index=cisco ... | rex ....
| mvexpand ip0
| streamstats count as row by _time
| eval row="ip".row
| eval {row}=ip0
| fields - ip0
| stats values(ip*) as ip* by _time- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
still doesn't work, return with job error
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What is the error? Start with your initial search and keep adding lines one at a time to see where the error gets introduced
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you, problem is solved