- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How to replace a string with RegEx in search resul...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have my Sonicwall logfiles coming into Splunk. By searching this index I want to replace "dst" (Destination IP address) without portnumber and interface with (for example) RegEx. Note that the formats used for "src" and "dst" = (ip address):(port number):(interface)
So when I do a search like (NOTE: the red sentence is my own attempt, however, it does not give a result I had in mind.):
index=sonicwall msg="Connection Opened" OR msg="Connection Closed" earliest=-2m latest=-1m
| eval dst=if(match(dst, "\d{1,3}.\d{1,3}.\d{1,3}.\d{1,3}:\d{1,5}:X\d{1}"), dst, replace(dst, "(\d{1,3}.\d{1,3}.\d{1,3}.\d{1,3}):\d{1,5}:X\d{1}","\1"))
| stats first(_time) as _time by src dst proto msg
| inputlookup append=t firewall_open_connections
| fillnull msg value="Connection Opened"
| eval closed=if(msg="Connection Closed",_time,"1")
| eval open=if(msg="Connection Opened",_time,"1")
| stats first(open) as open first(closed) as closed by src dst proto
| where open > closed
| rename open as _time
| fields src dst proto _time
| outputlookup firewall_open_connections
Results in:
10.0.1.5:50492:X2 | 8.8.8.8:53:X1 | udp/dns | 2022-06-14 15:40:08 |
192.168.1.100:37016:X0 | 54.81.233.206:443:X1 | tcp/https | 2022-06-14 15:39:01 |
192.168.1.100:38376:X0 | 104.244.42.130:443:X1 | tcp/https | 2022-06-14 14:49:14 |
192.168.1.100:38611:X0 | 172.217.132.170:443:X1 | udp/https | 2022-06-14 15:37:51 |
Now I would like the "dst" results to be stripped of :(port number):(interface)or :(interface). In other words, only the IP address should remain
How do I do that within my query in Splunk with for example RegEx (or another method)?
Any tip is welcome, am very new to Splunk.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can use replace() function to trim everything from the semicolon to the end of the field.
| eval dst=replace(dst,":.*","")
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can use replace() function to trim everything from the semicolon to the end of the field.
| eval dst=replace(dst,":.*","")
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you, this is a simple and effective way that I was looking for. Really appreciate it.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
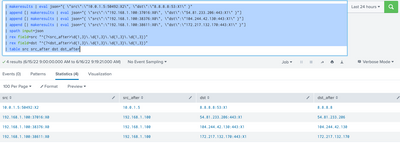
Hi, I think you want to use the rex command here. In my example below, I am taking the leading four octets of src and dst and putting them into new fields named src_after and dst_after. Everything after the first four octets is ignored. All of the stuff in |makeresults and |spath is just for me to build up some fake data using what you provided. The part you want to look at starts with the |rex steps. I hope this helps.
| makeresults | eval json="{ \"src\":\"10.0.1.5:50492:X2\", \"dst\":\"8.8.8.8:53:X1\" }"
| append [| makeresults | eval json="{ \"src\":\"192.168.1.100:37016:X0\", \"dst\":\"54.81.233.206:443:X1\" }"]
| append [| makeresults | eval json="{ \"src\":\"192.168.1.100:38376:X0\", \"dst\":\"104.244.42.130:443:X1\" }"]
| append [| makeresults | eval json="{ \"src\":\"192.168.1.100:38611:X0\", \"dst\":\"172.217.132.170:443:X1\" }"]
| spath input=json
| rex field=src "^(?<src_after>\d{1,3}\.\d{1,3}\.\d{1,3}\.\d{1,3})"
| rex field=dst "^(?<dst_after>\d{1,3}\.\d{1,3}\.\d{1,3}\.\d{1,3})"
| table src src_after dst dst_after
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for your answer. Definitely much appreciated. However, this is not the solution I was looking for because I have to change everything myself or include it in a regex list. However, the examples in my post were only a few lines, but the actual result is thousands of lines.