- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How to get logs to show fieldnames
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi everyone!
I'm still fairly new to Splunk so sorry if it is a simple question.
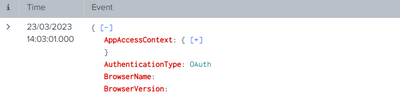
I have some logs that does not show the field names when you have done a search.
But when I expand the event, I can see the names.
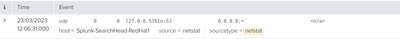
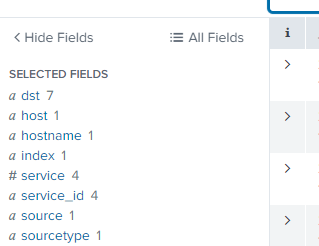
Is it not possible to have the field names shown in the first picture?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, you can do that using a search command, like this
... your base search ...
| fields *
| tojson
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @NJ ,
are you using Verbose or Smart Mode in your search?
you have to use Verbose Mode to display all the extracted fields.
if you have in interesting fields less fields than all fields the reason is that probably you have less results than 20%, so they aren't visualized in interesting fields.
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
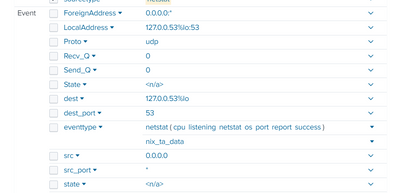
Hi @gcusello
I can see the field names on the left side but I was wondering if I would be able to see them in the event list like this:
Field name: Value
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @NJ ,
you can visualize logs in raw text mode.
If you want to visualize them in json format, you have to manually open each of them, for my knowledge there isn't an option to open all the sub parts of the log.
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
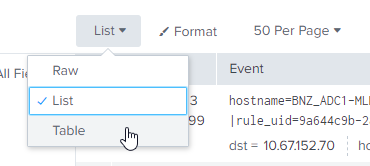
Hi @NJ
The List view will just show you what the event data looks like as it was ingested. There obviously must be some automatic field extraction going on for the field values to be extracted.
If you want column headers (field names) to show with the values underneath, then you can pick the table view instead
Whatever you have as Selected Fields will show as a column with the value underneath.
You can select or deselect fields by clicking into them.
Another method, though is to use the table command
...your search ...
| table *You can specify the field names you want or just use the * wildcard for everything.
Hope this helps. Please mark as solution provided if this answer your query.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
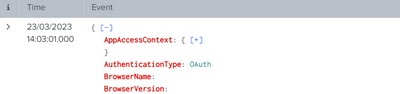
Hi @yeahnah
Thanks for your reply learned something new!
However, is there no way to get it like this JSON example:
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, you can do that using a search command, like this
... your base search ...
| fields *
| tojson
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just be aware that you're not showing the original event anymore - just some rendered json structure.