Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Splunk Search
×
Are you a member of the Splunk Community?
Sign in or Register with your Splunk account to get your questions answered, access valuable resources and connect with experts!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: Find the time difference between the event an...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to find the time difference between the event and the current time?
alexspunkshell
Contributor
04-25-2022
02:51 AM
I have " threatInfo.updatedAt" information in my logs.
I want to get an alert if the time difference between "threatInfo.updatedAt" & "_time" is more than 4 hours.
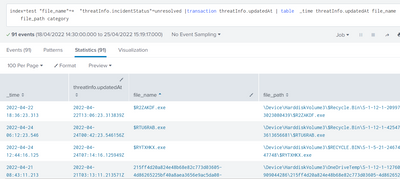
My Search Query
index=test "file_name"=* "threatInfo.incidentStatus"=unresolved |transaction threatInfo.updatedAt | table _time threatInfo.updatedAt file_name file_path category
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
PickleRick

SplunkTrust
04-25-2022
03:03 AM
| eval updatedat=strptime(threatInfo.updatedAt,"i never remember those formats ;)")
| where abs(_time-updatedat)<4*3600
I really can never remember those time format specifiers.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
isoutamo

SplunkTrust
04-25-2022
03:27 AM
Link to those: https://docs.splunk.com/Documentation/Splunk/latest/SearchReference/Commontimeformatvariables
In your case: "%Y-%m-%dT%H:%M:%S.%6Q%Z" or same in shorter format "%FT%T.%6Q%Z"
r. Ismo
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
PickleRick

SplunkTrust
04-25-2022
03:41 AM
Thanks. 🙂 As usual, I was typing it on my tablet and it's very inconvenient to switch between different tabs there.
Get Updates on the Splunk Community!
Shape the Future of Splunk: Join the Product Research Lab!
Join the Splunk Product Research Lab and connect with us in the Slack channel #product-research-lab to get ...
Auto-Injector for Everything Else: Making OpenTelemetry Truly Universal
You might have seen Splunk’s recent announcement about donating the OpenTelemetry Injector to the ...
[Puzzles] Solve, Learn, Repeat: Character substitutions with Regular Expressions
This challenge was first posted on Slack #puzzles channelFor BORE at .conf23, we had a puzzle question which ...