- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How to extract value from a field?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Good Afternoon!
I have a search (code example #1) that looks for the EventData_Xml field looking at programs installed. I'm creating a report to show what where and when. Trying to cut out the unneeded data and show just the program name, such as Microsoft Edge in the "Program Installed" column in the code example #2 below.
Thank you in advance for any assistance. I appreciate it.
index=wineventlog EventData_Xml="*" AND EventID=11707
| table host _time EventData_Xml
| rename host as "Host", _time as "Time", EventData_Xml as "Program Installed"
| convert ctime(Time)<Data>Product: Microsoft Edge -- Installation completed successfully.</Data><Data>(NULL)</Data><Data>(NULL)</Data><Data>(NULL)</Data><Data>(NULL)</Data><Data>(NULL)</Data><Data></Data><Binary>7B34443639394544332D333539302D334635352D424638302D3732374546444242313032467D</Binary>
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The rex command can do that.
index=wineventlog EventData_Xml="*" AND EventID=11707
| rex field=EventData_Xml "Product: (?<Product>[^-]+)"
| table host _time Product
| rename host as "Host", _time as "Time", Product as "Program Installed"
| convert ctime(Time)
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The rex command can do that.
index=wineventlog EventData_Xml="*" AND EventID=11707
| rex field=EventData_Xml "Product: (?<Product>[^-]+)"
| table host _time Product
| rename host as "Host", _time as "Time", Product as "Program Installed"
| convert ctime(Time)
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
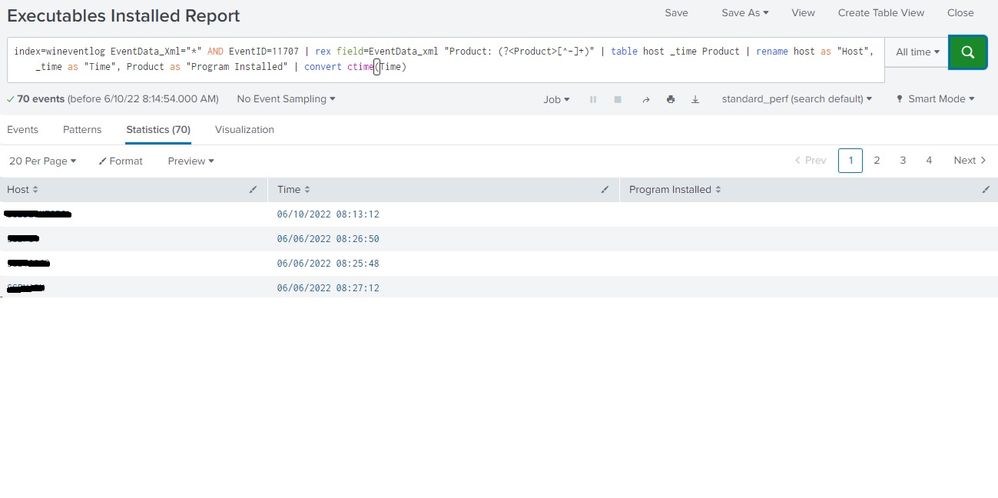
This is what I get with that string. This is the problem row. Thank you for your help.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There was a typo in my answer. I've fixed it.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Any thoughts on sorting by time descending? I've tried a few different ways and it only sorts by the month at the beginning with 1 on top or 12 on top but not accurate to the whole date.
I've tried | sort _time desc and asc and few other variations. Thank you.
Edit: Disregard, one well placed "| sort - _time" before the table sorted by desc.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you very much! Looks nice and clean now. 🙂
