- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: How to calculate max of transaction from sum o...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to calculate max of transaction from sum of 2 fields?
Currently I am trying to find the max of field (which is already a sum of 2 different fields). The problem unfolds as follows,
1. Variable C is Sum of Variables A & B
2. Variable A is result of sum of transactions in last 30mins and Variable B is sum of transactions in last 30mins
Splunk helps to calculate the total of A+B, average of the same at each transaction level). But when I tried to find max of transaction (to understand a peak value within 30mins at total level (i.e. variable C), by default the tool points me to the total value, which is not the correct answer. We need to understand the transaction values (multiple values of C) and then find the max of C.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
There's probably a couple of ways to do this, depending on how you want to output to look at the end.
One option is using appendpipe and stats as a replacement to addcoltotals (which is what I'm guessing you're using).
Here's an example (you can ignore the makeresults and append stuff, the first 7 lines, that's just to simulate your data):
| makeresults count=1
| eval bytessent=30 | eval bytesreceived=40 | eval xtime="00:15"
| append [| makeresults count=1
| eval bytessent=40 | eval bytesreceived=40 | eval xtime="00:30"]
| append [| makeresults count=1
| eval bytessent=50 | eval bytesreceived=50 | eval xtime="00:45"]
| fields - _time
| eval totalbytes=bytessent+bytesreceived
| eventstats max(totalbytes) as maxbytes
| appendpipe [| stats sum(bytesreceived) as bytesreceived sum(bytessent) as bytessent sum(totalbytes) as totalbytes max(maxbytes) as maxbytes]
| table xtime bytesreceived bytessent totalbytes maxbytes
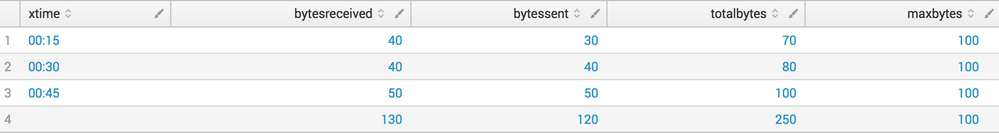
This would give a table that looks like this:
As you mentioned eventstats, it sounds like you were already 90% of the way there anyway.
I hope that gets you closer to what you're looking for.
Graham.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The challenge here is that, we could get these transaction values with simple syntax like eventstats, stats..but after all theses when we target to address the total column, by default only 1 value is getting populated here. But we don't wanna a single value. The reason is, total column could be misleading with any other max value in the interim time or a peak/spike value within the selected period. So, the "max" value in "total" should work in a similar way we execute 'eventstats' for other columns.
The current code executes the max value (undoubtedly!), since we depend on only 1 value in 'max' variable, we happen to see the same value for any no of transactions within the stipulated time period.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The dataset sample looks as follows,
_time bytessent(A) bytesreceived(B) totalbytes(C)
0:15:000 30 40 70
0:30:000 40 40 80
0:45:000 50 50 100
1:00:000 60 50 110
1:15:000 20 70 90
Total 200 250 450
Column A is sum of transaction in last 30mins, and B is sum of bytes received in last 30mins. By using <|bucket span=20m> will help us to get the sum value of transactions in last 30mins for A & B. But when tried using but the result is that 'max' value feeds only on final summation value (A+B) rather than the individual max in column 'C'. From above e.g. max(C) should be 110, but eventstats of C gives 450 as max value. This is not the right answer. So, we need to assess the transaction level details even after totaling.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You need to remove the part of search where you're calculating the Total and move it after your eventstats max(... part.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We need to see your current search, and may be sample events, in order to understand the situation better and suggest a solution.